The Libre-Halaal ByStar Digital Ecosystem
The Libre-Halaal ByStar Digital Ecosystem
A Unified and Non-Proprietary Model For Autonomous Internet Services
A Moral Alterantive To The Proprietary American Digital Ecosystem
| Document Number: | PLPC-180016 [ .bib ] |
| Version: | 0.6 |
| Dated: | September 5, 2013 |
| Group: | general |
| Primary URL: | http://www.by-star.net/PLPC/180016 |
| Federated Publications: | ByTopic -- ByContent |
| AccessPage Revision: | This AccessPage was produced on December 04, 2016 at 17:15 PST (-0800) |
| Author(s): | Mohsen BANAN |
| Organization: | Neda Communications, Inc. |
AVAILABLE FORMATS
- PDF: -- 384K -- Provides the document in Portable Document Format.
- HTML: -- 488K -- Displays the document as a web page.
AVAILABLE OTHER FORMS
- articleEnFa.pdf: -- 384K -- .
- presentationEnFa.pdf: -- 100K -- .
- emailContentEnFa.pdf: -- 368K -- .
SHORT
DESCRIPTION
The Libre-Halaal ByStar Digital Ecosystem is presented as a unified and non-proprietary model for autonomous internet services and a moral alternative to the Proprietary American Digital Ecosystem.
A Unified and Non-Proprietary Model For Autonomous Internet Services
A Moral Alterantive To The Proprietary American Digital Ecosystem
Version 0.6
September 5, 2013
http://www.by-star.net/PLPC/180016
http://www.neda.com/PLPC/180016
http://www.freeprotocols.org/PLPC/180016
Copyright ©2012,2013 Neda Communications, Inc.
Permission is granted to make and distribute complete (not partial)
verbatim copies of this document provided that the copyright notice
and this permission notice are preserved on all copies.
For Preservation Of The Individual’s Autonomy and Privacy
[ This web page is also available in pdf format as PLPC-180016. ]
Dear Fellow World Citizen,
In the Proprietary American Digital Ecosystem (Internet Application Services as they exist today), the individual’s autonomy and privacy are being crushed. A deal has been made. Users free-of-charge get: email, calendar, address book, content publication, and Facebook friends. In return, American corporations get: semantic analysis of email, spying with consent, traffic, logs and trail analysis and behavior cross referencing.
A new currency has been created. The user’s autonomy and privacy is now the implicit Internet currency. For now, the established business model is that of translation of the individual’s privacy into targeted advertising. That business model will naturally grow in scope. The debit side of this new currency is civilization and humanity.
Today, the world is largely unaware of this. The public is completely oblivious to the perils of the proprietary Internet model, and happily entrusts its personal data, its privacy, its freedoms and its civil liberties to proprietary business interests. And the people whose responsibility it is to safeguard the public interest – government, and the engineering profession – are asleep at the wheel. Or worse yet, they have become accomplices.
In addition, Internet services are inconsistent, disparate and incoherent. Resulting into 10s of passwords for the individual on services over which she has no real control. The dynamics and trends of the Proprietary American Digital Ecosystem are such that autonomy and privacy of the individual will continue to deteriorate.
This is about rescuing humanity from the dragnet of Google, Facebook and America’s surveillance economy. Our primary offerings are real, tangible and practical autonomy and privacy – on very large scale.
We are Internet Engineers. We know that we can design and create a complete parallel digital ecosystem which preserves the individual’s autonomy and privacy – to compete with and stand against the existing Proprietary American Digital Ecosystem. And we have done so.
But to put it in its intended widespread usage, we also need your participation (our fellow engineers, journalists, financiers, academics, government representatives, ethicists and users). Preservation of autonomy and privacy are multi-dimensional. So, we have taken it upon ourselves to also consider philosophical, moral, societal, social, economic and business dimensions of our parallel digital ecosystem.
The umbrella title that we have chosen for our work is:
The Libre-Halaal ByStar Digital Ecosystem
A Unified and Non-Proprietary Model For Autonomous Internet Services
A Moral Alternative To The Proprietary American Digital Ecosystem
http://www.by-star.net/PLPC/180016 — [9]
ByStar (By* – pronounced by-star) is based on the model of Federations of Autonomous Libre-Halaal Services and is being presented as a moral alternative to the American Proprietary Digital Ecosystem.
The totality of Libre-Halaal software, Libre-Halaal Internet services, content generation and publication facilities and societal frameworks that we describe are designed for preservation of ByStar user’s autonomy, privacy and freedom. The health of society is our objective. This is not about rejection or prohibition or censorship of Internet. This is about creation of a parallel digital ecosystem within the Internet based on values which are very different from the economically driven proprietary American digital ecosystem.
By “Digital Ecosystem”, we mean the whole thing, including inter-related software, systems, services, content and societal frameworks. The integrated facilities of ByStar are intended to be used by a very large segment of population on this planet. The scope of these integrated offerings is vast – paralleling most of what exists in the proprietary Internet today.
The parallels include:
- A functional equivalent of Gmail that recognizes your mailbox must be autonomous and private.
- A functional equivalent of Facebook that respects your privacy.
- A functional equivalent of YouTube that recognizes your content as yours.
- A functional equivalent of Windows that creates a deep Software-Service continuum.
In the ByStar model these capabilities are unified, consistent and coherent.
This is not about any new particular functionality. It is not a faster, cheaper, better story. In terms of functionality, what we offer is generally same as what exists today. Our model provides for the existing functionalities, while offering tangible autonomy and tangible privacy.
There is nothing anti-business about our offerings and our moral stands. The ByStar business model is simply different from the current dominant American business models of exploiting privacy and autonomy. We are in the business of providing autonomy and privacy. And there is plenty of money in that. Broad and deep usage of our software and our Internet application services will create revenue opportunities that are similar to those of large Internet application service providers today. These revenues include subscriber fees, advertising, customization consultation, general consultation and interaction facilitation fees. Profit, business and economics are an integral part of ByStar.
Key distinguishing aspects of our approach and software and services are:
- Preservation of the individual’s autonomy. ByStar services are inherently autonomous. They belong to their owner-user – not the service provider.
- Preservation of the individual’s privacy. The individual is in full control of her service. She can fully control her privacy.
- They are comprehensive, unified, consistent and cohesive. The scope of ByStar is everything. The “*” in By* comes from the glob expansion symbol. And all these services are unified with the ByStarEntity model.
- They are rooted in the correct manner-of-existence of software and services. The entirety of ByStar software and services are internally transparent. ByStar software and services development process is fully collaborative. Based on the nature of poly-existentials, ByStar ideology fully rejects the Western Intellectual Proprietary Rights regime.
In other words, morality, health of society, and well being of humanity are an integral part of software and services that we offer. This work is primarily not Businessman driven. It is Engineer driven.
We believe that privacy, autonomy and freedom aspects of the Digital Ecosystem that we are creating are important enough to “convert” many existing proprietary service users to become Libre-Halaal ByStar users. All attempts at claiming autonomy and privacy in the proprietary model are hollow at most. It is not possible to offer real and tangible autonomy and privacy without committing to complete internal transparency of software and services. The proprietary model leads to dark software and dark services (internally opaque) which are inherently anti-autonomy and anti-privacy.
Such a large undertaking by such a small group should normally amount to not much more than pipe dreams. Typical first reaction to our claim is a chuckle. Some say it is insane. Many say that the notion of creating a parallel digital ecosystem is so very lofty that it can’t be realistic.
There are several reasons why we believe widespread usage of what we are building is more than plausible. It is viable and likely.
- ByStar ideology is in harmony with nature. We understand the enormous, seismic force that accompanies halaal manner-of-existence of software and halaal manner-of-existence of Internet services (as expressed in the Libre-Halaal label). Manifestations of this force include the Free Software Movement and GNU/Linux. But there is far more to come.
- We have already built the needed framework and starting points. These are in place and are growing.
- The ByStar model grand design is broad, evolutionary, expandable and it can grow to scale to planet wide usage.
- The demand for autonomy and privacy are very real. Many are starting to recognize that things like Facebook are very wrong. Healthy alternatives are craved.
- The business and economic models for ByStar have been thought through and are being cultivated.
There are two fundamental concepts at the core of what we are presenting and offering:
- Humans are more than just economic creatures. Internet’s model can not be based on pure economics.
- The Western Intellectual Property Rights (IPR) regime is a colossal mistake – Western IPR laws are in conflict with nature and detrimental to civilization.
If you are unable or unwilling to explore the truth behind these basic concepts, then ByStar is likely not for you.
If you recognize the critical distinction between humans and economic creatures, and if you recognize the basic human need for autonomy and privacy, and if you are willing to explore the rejection of the Western IPR regime, then the Libre-Halaal ByStar Digital Ecosystem could well be for you.
Contents
- 1 Problem: Individual’s Autonomy and Privacy Are Being Crushed
- 2 Overview Of Digital Ecosystems
- 3 The Proprietary American Digital Ecosystem
- 4 The Libre-Halaal ByStar Digital Ecosystem
-
4.1 ByStar Ideology: The Libre-Halaal Philosophy
- 4.1.1 Halaal and Haraam and The Libre-Halaal Label
- 4.1.2 Guardianship Of Internet By The Engineering Profession
- 4.1.3 Nature Of Poly-Existentials: Basis For Abolishment Of Western IPR Regime
- 4.1.4 Libre-Halaal Software – Halaal Manner-Of-Existence Of Software
- 4.1.5 Libre-Halaal Internet Services – Halaal Manner-Of-Existence Of Internet Services
- 4.2 ByStar Applied Model Of Federations of Autonomous Libre-Halaal Services
- 4.2.1 The ByStar Reference Model
- 4.2.2 Domain Name Bindings Of ByStarEntity
- 4.2.3 ByStar Autonomous Services
- 4.2.4 ByStar Controlled Services – Internet Of Things
- 4.2.5 ByStar Federated Services
- 4.2.6 ByStar Convivial User Environments – Blee and BxGnome
- 4.2.7 ByStar Content Generation and Content Publication Facilities
- 4.3 ByStar Architecture Principles
- 4.4 ByStar Central
- 4.5 Current ByStar Services and Capabilities
- 4.6 Relationship With Existing Realities
- 4.7 ByStar Economics
- 4.8 Understanding The Full ByStar Picture
-
4.1 ByStar Ideology: The Libre-Halaal Philosophy
- 5 ByStarEntity Realization Models – By Way Of Some Examples
- 5.1 ByStarEntityId Registrations
- 5.2 Shared Cloud Autonomous Model
- 5.3 Hosted Private Cloud Autonomous Model
- 5.4 Premise Private Cloud Autonomous Model
- 5.5 ByStar Autonomous Services Use and Access Examples
- 5.6 Some Examples Of ByStar Autonomous Services Capabilities
- 5.7 ByStar Federated Services Examples
- 5.8 Bob And Alice’s ByStar Digital Ecosystem
- 6 Dynamics of the Libre-Halaal vs. Proprietary-Haraam Battle
- 7 Our Responsibilities and Your Participation
- 8 Joining ByStar
1 Problem: Individual’s Autonomy and Privacy Are Being Crushed
Today, the Internet services industry is almost entirely owned and controlled by proprietary commercial interests. Google, Yahoo, MSN, LinkedIn, YouTube, Facebook, Apple, and virtually every other Internet service—these are all proprietary for-profit corporations, with no obligation towards the public welfare.
This represents a grave hazard to the broader interests of society. The existing proprietary digital ecosystem is well on its way towards the destruction of humanity. Under immediate threat of destruction are the privacy of the individual, and the autonomy of the individual.
Loss of autonomy and privacy are symptoms of the basic model of the Proprietary American Digital Ecosystem. At societal level, autonomy and privacy can not be preserved just with new technology. There are no band-aid technical solutions.
The basic model of the Proprietary American Digital Ecosystem is all wrong.
There is already the beginning of dawning realization within society of the growing danger to the individual’s rights and freedoms.
Various attempts at blowing the whistle are made by some, but these are often crude and lack understanding of root of the problem.
1.1 Early Shallow Recognitions Of The Problem
Some such superficial expressions of the problem include:
Julian Assange (in 2012) puts it like this:
The world is not sliding, but galloping into a new transnational dystopia. This development has not been properly recognized outside of national security circles. It has been hidden by secrecy, complexity and scale. The Internet, our greatest tool of emancipation, has been transformed into the most dangerous facilitator of totalitarianism we have ever seen. The Internet is a threat to human civilization.
Eben Moglen (2011) says:
Zuckerberg has done more harm to the human race than anyone else his age.
Moglen (2011) also says:
Facebook is Wrong. It should not be allowed. You technologists should fix this.
Scott McNealy is quoted (1999) as saying:
You have zero privacy anyway. Get over it.
Tim Berners-Lee (2014) says:
We need to re-decentralise the Web.
Tim Berners-Lee (2014) is even willing to think of responsibilities of the “geek community as a whole” – but as a Westerner, he is apparently unable to recognize Software Engineering as a global profession with global responsibilities. So, he says:
It’s important to have the geek community as a whole think about its responsibility and what it can do.
Even the British Sir Elton John, who has made his fortunes from copyright restrictions, now kind of gets it. When it comes to pharmaceutical companies profiting from the miseries of the sick through patent restrictions, Elton John says:
We must end the greed of these corporations.
Edward Snowden (2013) says:
“if a surveillance program produces information of value, it legitimizes it. . . . In one step, we’ve managed to justify the operation of the Panopticon.”
The Panopticon is a architectural concept for a prison where the guards can watch, unseen by the inmates, from a tower in the middle into all cells build in a circle around the tower. It leaves the inmates in a perceived state of permanent surveillance. The French philosopher Michel Foucault described the effect:
Hence the major effect of the Panopticon: to induce in the inmate a state of conscious and permanent visibility that assures the automatic functioning of power. So to arrange things that the surveillance is permanent in its effects, even if it is discontinuous in its action; that the perfection of power should tend to render its actual exercise unnecessary; that this architectural apparatus should be a machine for creating and sustaining a power relation independent of the person who exercises it; in short, that the inmates should be caught up in a power situation of which they are themselves the bearers.
The original Panopticon, like the digital versions the likes of NSA and Microsoft are building, takes away all feeling of privacy. Even when one is not watched, knowing that the possibility of being watched is always there, creates uncertainty and leads to self disciplining and self censorship. It is certainly a state the powers that be would like everyone, except themselves, to be in.
To call these signs of deterioration of humanity is an understatement.
1.2 Denial, Ambivalence, Ignorance, Inevitability and Acceptance
Many think that there is no problem.
Many Americans work for the likes of Facebook, Google, Microsoft, Yahoo, etc. Or they are related and dependent on these companies. If bread and butter of these companies was to become profiting from crushing autonomy and privacy of the individual, most of their employees would likely not have any interest in facing an honest mirror. That has already happened.
People are naturally good at justifying the morality of their self-interest in a variety of forms. Mass psychology then kicks in and reinforces short term interests towards global mass exploitation. It is an inherent characteristic of citizens of unchecked powers to confuse morality with self-interest. Consider America and Americans.
From the perspective of a drug dealer, use of drugs is no problem. Many drug pushers are drug users. They want every body to be using drugs. After all, it is a profitable business and economics is the basis of everything. When someone tells them that subjecting cocaine to business and economics is wrong, the drug dealer does not have the ear for it.
Individual’s autonomy and privacy are not market commodities. They are part of humanity. The problem that we are pointing to is a human problem. This could well not be a problem for economic creatures existing in an industrial context — that is how pure raw American capitalism is viewed by many.
This sort of thing happens gradually. People become accustomed to the problem. They become dependent on the problem. They become the problem. The next generation is born into it. And then there is no problem.
Everybody does it. Everybody is on Facebook. What problem?
The public at large, and the young in particular, follows and is manipulated. They sit in awe of Internet technology. Ignorant, they trust the specialists who are there to milk their soul. The latest gadget and the latest Internet feature includes exploitation of another aspect of their privacy. They feel in charge while being used. And they feel empowered.
The concept that these very same awesome capabilities and technology can exist in a healthy context is foreign to the public at large. Industrial tools is all that they have seen, Tools for Conviviality, [2], is Greek to them.
Others kind of see the problem but consider it inevitable. More recently, discussions of loss of privacy in the context of Internet services has become a daily occurrence in mainstream western press. None of these discussions has any depth and no meaningful cure is even searched for. Many articles and books have been written about “End of Privacy.” Shallow, subdued nagging – that is the position and role of American press on the problem.
1.3 Some Fringe, Shallow And Simplistic Partial Solutions
There have been various engineering efforts to address these problems. Because these efforts are mostly just engineering centric, at best, they have proven to be limited in scope and at most peripheral.
Most of these efforts are Western in origin and focus on “freedom”, and are limited in their analysis and scope.
- FOSS/FLOSS Movement:
-
Some software engineers have instinctly recognized that the open-source manner-of-existence of software is advantages to software engineers and software engineering.These group of software engineers have attempted and mostly failed to frame this topic at societal level.
In the meantime, proprietary corporate America has figured out various ways of bastardizing FOSS and its fruits. Some such examples include, Tivoization, Appelization and servicization.
- Linux – Debia/Ubuntu/etc Distros:
-
Over time FOSS/FLOSS movement have produced a complete operating system, where in the software arena, we now have a complete solution that can compete with proprietary software.But, in the meantime the arena has shifted from software to services.
- Freedom Oriented Component Projects (Tor, etc) :
-
Various projects provide some useful partial solutions at component level.For example, the Tor software protects you by bouncing your communications around a distributed network of relays run by volunteers all around the world: it prevents somebody watching your Internet connection from learning what sites you visit, it prevents the sites you visit from learning your physical location, and it lets you access sites which are blocked.
- FreedomBox Project:
-
In order to combine the results of various of these freedom oriented component projects, the FreedomBox attempts to create an umbrella profile. Yet it fails to recognize that what is needed is not just the box but a full digital ecosystem.
None of these attempts have recognized that the problem needs to be addressed as the complete digital ecosystem level and at societal level. Most of these attempts fundamentally come from the American and Western model of thinking and analysis.
1.4 Root Causes Of The Problem
The Internet has its origins in America. In the beginning, the Internet was a healthy Engineering construct – and we played a minor role in its formation. The initial model of the Internet was rooted in the end-to-end model of interactions between autonomous entities/individuals, but things changed quickly. The Internet became a business construct. Now, the current basic model of Internet is rooted in the rise-of-the-middle model of corporations exploiting the individual.
Today’s Internet has been shaped by Proprietary American values. And this is the root cause of the problem. In particular, the Proprietary American Internet model is based on:
- Supremacy of business and economics – Leaving no room for societal, social, philosophical or moral considerations in the base fabric of society.
- Errant American copyright and patent law sourced from the US Constitution – Ramifications of such grave ownership mistakes are complex and long lasting. But, they can be even more harmful than the previous American ownership mistake – American slavery.
- Unbounded Corporations. The Corporation, an entity whose sole purpose is to generate profit is permitted to do all that it pleases and in many respects is considered equivalent with human individuals. This model reduces humans to the level of Corporations – greed driven psychopathes.
- Elimination or marginalization of role of Professions (Internet Engineering) in society.
- Corpocracy – Where collaboration of Corporation and Government results in manipulation and control of the People.
- Extreme Individualism – Rampant Self-Toxication At Epidemic Levels. Stressing personal freedoms, out of balance against significance of health of society and humanity, play well into manipulation of individuals by corporations.
- Uses of Internet as an instrument to exploit other societies and cultures. Based on American Exceptionalism.
These dynamics are such that Proprietary American Internet model puts not just America, but the entirety of human civilization in danger.
We will refer to the above American spheres of consensus that shape the core of American character as "The Proprietary American Regime" – and sometimes just "The American Regime" or “Americanism”. It is the belief system and not Americans as individuals that we are referring to – while recognizing that the core of character of most American individuals shapes the American Regime and is shaped by it. Furthermore, the belief system that we call "Americanism" physically and geographically spans far further than the United States of America. Many through out the world have been inflicted by this disease and are “Americanized”.
The American Internet model is being portrayed to the world as universal. It is not. There is more to the world than the American Regime. The American Regime has produced well understood results for other crucial aspects of life that the civilized world has fully rejected. Much of the world wishes to be separate from the American Regime.
Consider how Americans eat. The American “Food Inc.” model has turned the American farmer into instruments of agro-business machinery of patented economic processes. Partaking food by humans has been turned into manipulation of the economic creatures by the business. Human beings have been turned into economic creatures existing in an industrial context for the purpose of the business of consuming food. Obesity is prevalent amongst the poor in America.
Consider how Americans take care of their sick. Health and medicine has been fully subjected to capitalism. Everyone for himself. The doctor-patient relationship has become a fully economic transaction. Insurance business has been placed on the top and the patient at the very bottom while the American doctor has become nothing more than a tool of business. The rich think that this works very well for them. In the aggregate, it is a miserable failure. For example, Cuba with a fraction of resources produces infant mortality rate results that compare very well against the American Regime’s. The obvious human model of universal health care which is practiced through out the civilized world is considered nasty socialism in America.
Consider how Americans view prescription medications. The Anglo-American culture permits advertising of prescription drugs on Television. Nowhere else in the world is this permitted. The exclusive producer of the patented medication is permitted to dangle the cure in front of the sick – in public. The profession of medicine is by-passed by the business where the sick is encouraged to tell the doctor what to do.
Consider how Americans consider university education. The average American graduate comes out $35K in debt. The purpose of education has become preparation for economic activity. In the American model, learning too has become a purely economic activity.
Consider how Americans view their guns. When extreme individualism is at the center, ridiculous arguments for ridiculous freedoms become the norm. The distance from there, to “going postal”, “Columbine”, “Sandy Hook”, etc. is very little.
Consider how Americans view relations with other societies. America’s short history points to exploitation, colonialism, dominance and imperialism as clear trends. The natives are now concentrated in reservations. The African continent has been destroyed and the African languages and cultures were bulldozed into oblivion. Descendants of those African slaves are now a majority in American prisons. The use of the atomic bomb, the ultimate weapon of mass destruction, was initiated by Americans. The CIA’s clandestine coups to manipulate and exploit Iranians, Arabs, South-Americans, etc. are celebrated and glamorized through the Jewish-American Hollywood. The patterns of Vietnam, Iraq and Afghanistan point to the inability of Americans to listen, understand and learn.
Much of the civilized world has looked at these American models and has fully rejected them.
When Americans try to impose their models on others, rejections of these American models by the rest of the world, often takes the form of: “Yankee Go Home”, “Go To Hell Yankee” and “Death To America” chants followed by physical rejection and separation. And that has kind of worked for some – e.g., the 1979 Iranian Revolution.
The Japanese/Brazilian/Iranian/Chinese/French/Cuban/Indian/Russian/etc models for food, medicine, university education and guns are distinctly different from the American model. Much of the civilized world looks at the American model and sees a purely economicly oriented savage model. This of course is very different from what Americans see when they look in the mirror. This degree of self-absorption and these extremes of American monocultures of the mind are genuinely exceptional.
Given these trends, should the world accept the American Regime’s model for the global Internet?
Unlike, food, guns and medicine (mono-existentials) which are inherently local, the inherent digital (poly-existential) nature of Internet is global. Adoption of the purely proprietary American model of Internet puts civilization and humanity in danger.
Rejection of the American proprietary model of the Internet is far more complicated than rejecting the local American models of food, medicine, guns, etc. Slogans and chants are ineffective and complete physical separation is impractical. A large segment of the planet has already come to recognize that the greatest threat to humanity is Americanism. It is wholy wrong to allow the Proprietary American Internet to become a propagation vehicle for Americanism. It should not be permitted.
Our Anti-American tone here is not against Americans as individuals. American individuals who disagree with our root cause analysis, may continue their use of their proprietary American digital ecosystem.
The cure that we offer below is for all of humanity and is equally applicable to American individuals who recognize the disease.
1.5 Contours Of The Cure
In order to cure this disease, we need to conceptualize it in its totality – that of a “Digital Ecosystem”.
The Proprietary American Digital Ecosystem can not be fixed. Its dynamics are taking it to a particular eventuality – destruction of civilization and humanity.
Instead we need to erect an alternative digital ecosystem to stand against it.
The model of this healthy alternative digital ecosystem must be based on:
- Sanctity of autonomy and privacy – based on just morality and principle.
- Ideology of guardianship of the Internet by the engineering profession.
- Full rejection of Western IPR regime.
- Correct/Healthy manner-of-existence of software and services.
- Tangible assertion of autonomy.
- End-to-End Inter-Autonomous Confidentiality.
- Audit Trail Protection and Traffic Flow Confidentiality.
- Recognition of independence of societies and cultures.
- Full consideration of business and economics.
Consistent with these, we put forward the “Libre-Halaal ByStar Digital Ecosystem”.
2 Overview Of Digital Ecosystems
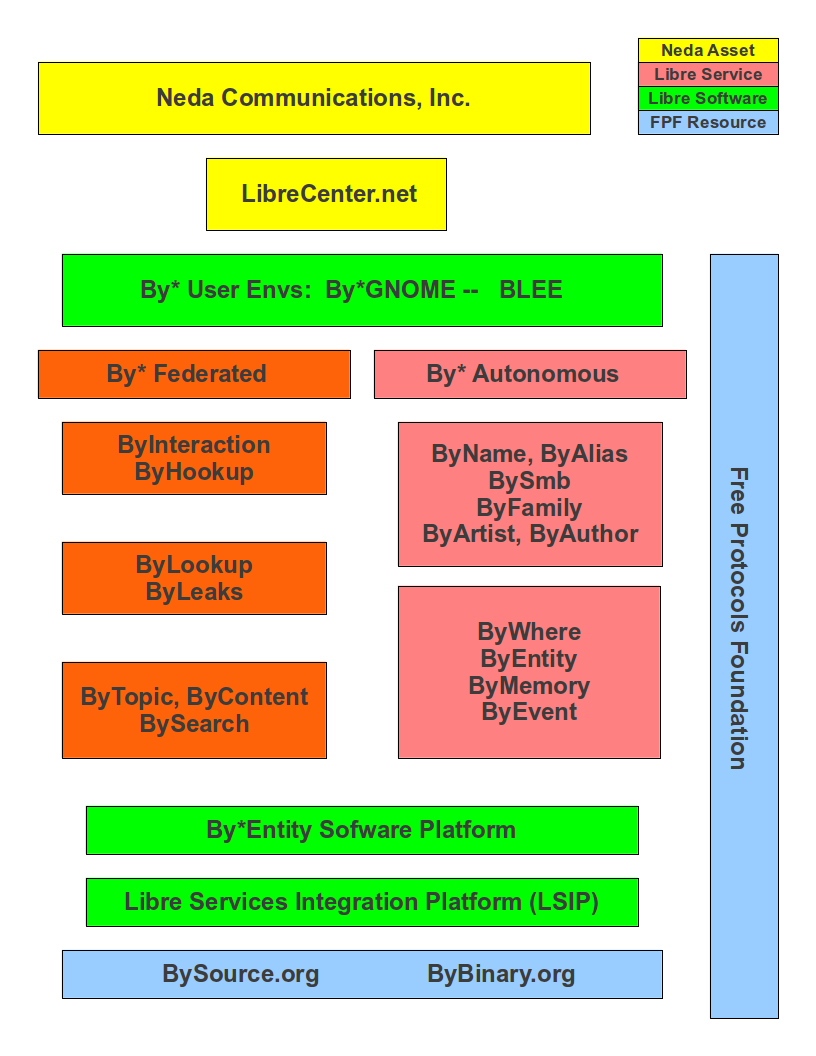
Figure 1: Parts Of The Libre-Halaal ByStar Digital Ecosystem
Our use of the term “Digital Ecosystem” is very broad and includes inter-related software, systems, services, content and societal frameworks including: philosophical, moral, societal, social, economic, business and legal practices – that shape it and are shaped by it.
Here we describe digital ecosystems in four parts.
- Ideology – Societal Frameworks:
-
Digital Ecosystems exist within societal frameworks. Digital Ecosystems are shaped by societal norms and Digital Ecosystems shape people and society.Very important aspects of societal frameworks which have immediate impact on shape of digital ecosystems are laws and models governing poly-existentials. Societal Agreements governing all that is digital (and more broadly poly-existentials) in the West is based on the Intellectual Property (IP) regime. This has shaped the entirety of Western Digital Ecosystems.
- Software and Usage Environments:
-
Software is the digital form that controls other digital forms. As such, it is the foundation of digital ecosystems. - Internet Services:
-
Internet Services consist of software execution accessed through a network. As such, software may no longer be in the immediate possession of the user. Internet Services are therefore a distinct part of digital ecosystems – separate from Software. - Information and Content:
-
A primary purpose of digital ecosystems is to facilitate production and communication of information and content. In addition to the content itself, facilities and rules governing production, publication and access to content are a distinct part of digital ecosystems.
2.1 Manner-Of-Existence Of Digital Ecosystems
We then recognize two basic Manner-Of-Existence Of Digital Ecosystems.
- Proprietary Digital Ecosystems:
- Governed by laws and models for Poly-Existentials
which are:
- Rooted in the Western patent regime
- Rooted in the Western copyright regime
- Internally opaque
- Libre-Halaal Digital Ecosystems:
- Governed by laws and models for Poly-Existentials
which are:
- Consider knowledge as unownable and fully rejects the Western patent regime
- Consider the right to copy a basic human right and fully rejects the Western copyright regime
- Required to be internally transparent
In practice, today there are two established models for the manner-of-existence of software.
-
The Proprietary Software Model.
This model is exemplified by Microsoft Windows. It is based on a competitive development model, and dominated by American companies. It is protected and rooted in the corrupt Western so-called Intellectual Property Rights regime, in particular the twin ownership mechanisms of patent and copyright. It is opaque and prevents software users from knowing what their software is doing. Its distribution is controlled by its producer.
- The Libre-Halaal Software Model.
This model is exemplified by Debian GNU/Linux. It is based on a collaborative development model where software engineers worldwide work collectively to move the software forward. It rejects the corrupt Western so-called Intellectual Property Rights regime of patent and copyright. It is internally transparent and permits software users to know exactly what their software is doing. Its distribution is unrestricted.
Based on these two definitions we now analyze the current dominant “Proprietary American Digital Ecosystem” and the “Libre-Halaal ByStar Digital Ecosystem”
3 The Proprietary American Digital Ecosystem
The broad label that we use for Internet services and software as it exists and is practiced today, is: “The Proprietary American Digital Ecosystem”. We include the term American in this label not just because it is dominated by America, but because it is rooted in American values and American rules. The American purely economic model and widespread practices which are based on Western IPR regime has led to dominance of Internet by large American corporation and governance of the Internet through Corpocracy. These corrupt values and models are now being exported and forced on the rest of the world in the name of Internet.
The manner by which the Proprietary American Digital Ecosystem is shaped by American societal norms is multi-faceted. To better understand this, in Figure 2 we provide a layered model.
|
The American Proprietary Digital Ecosystem
Internet Services and Software As They Exist Today Trends: Loss Of Autonomy, Loss Of Privacy, Dominance Of Corportaions |
|
Competing Enclaves: Google, Microsoft, Apple, Facebook, Amazon
Never Ending Patent Wars and Copyright Battles |
|
Industrial Proprietary Islands Of Software-Service Continuum
Windows+BingEtc -- Chrome+Google -- Apple |
|
Centralized Proprietary Internet Services
Designed To Track: Privacy As Currency -- Dominated By Big Business |
|
Proprietary Manner-Of-Existence Of Internet Services
Internally Opaque and Non-Collaborative |
|
Proprietary Software
FOSS Movement -- Bastardizations Of FOSS By Big Business |
|
Western Intellectual Property Rights Regime -- Copyright, Patents
Never Ending Patent Wars |
|
Celebration Of Individualism, Raw Capitalism, Freedom, Materialism
Freedom Of Corporations, Corpocracy, Neo-Colonialism rooted in Exceptionalism |
Figure 2: The Proprietary American Digital Ecosystem (Layered Model)
The very same eight layers that are presented in 2 are the basis of the layered model that we present as a moral alternative in Section 4. Note that without recognizing and tackling the underlying root causes of the problems that the proprietary American digital ecosystem present, it is not possible to cure these problems. When the underlying nature of any public digital ecosystem is proprietary, it poses a danger to health of society.
In the following sections, we focus on specific aspects of the above layered model.
3.1 Competing Proprietary Digital Enclaves
The Proprietary American Digital Ecosystem comprises of a number of competing Proprietary Digital Enclaves. The proprietary Microsoft digital enclave is one such example. The Microsoft enclave has had its roots in the proprietary software business and is now trying to bring in proprietary services. The proprietary Google digital enclave is an other example. The Google enclave has had its roots in the proprietary search business and is now trying to integrate with more software and services. Apple, Facebook and Amazon are examples of other American Digital Enclaves. What they all have in common is that they are all competing locked environment driven by Patent and Copyright laws. None of these enclaves were designed ab-initio to be digital environments for humanity. All of these enclaves exist primarily to generate profit for their owners.
This model of being governed by competing proprietary enclaves is normal and even desired by most Americans. The American medical system is similarly structured and so is the American food system. From the outside, many view Americans as purely economic creatures that exist in an industrial context who are fully committed to supremacy of money. While the proprietary American digital ecosystem my be fine for Americans, it may not be for the rest of the world. Bits are without border and this American disease has been spreading.
Ramifications of manner-of-existence of the proprietary digital ecosystem, matters in two important ways. It matters in terms of service functionality—what the service itself is actually doing. And it matters in terms of policy—what the service provider is doing.
3.2 Ramifications On Service Functionality
Regarding service functionality: existing proprietary services such as Google, Yahoo, YouTube, Facebook, Microsoft, Apple, and virtually every other service—these are strictly controlled assets of their owning companies, heavily defended by patents and copyright. The software that runs the service is closed, such that the true service functionality is unknown. This means that the user of the service you have no knowledge of what the service is actually doing behind the scenes. For example, you have no knowledge of what the service is doing with your personal information. Every item of information you provide to the service, either implicitly or explicitly—every communication, every search query, every website visited, every mouse click—can be used by the service provider for unknown purposes, without your knowledge or consent.
3.3 Ramifications On Service Policy
Regarding policy: in principle, the service provider’s actions are constrained by the Service Agreement (Terms of Use, Privacy Policy, etc.) between the provider and user. However, these agreements are drafted by the provider’s corporate lawyers, consist of sophisticated legalese that few users read, and are heavily biased towards the interests of the provider. In particular, they are drafted without any formal representation or advocacy for the interests of the user.
Proprietary services are operated by corporations whose actions are driven purely by profit. This is the single ultimate purpose of the proprietary service provider, to which all other considerations come secondary. In particular, both functionality and policy are dictated wholly by this purpose, with no concession towards the interests of the individual user or the general public welfare, beyond what contributes directly or indirectly to profit.
This closed, profit-motivated and -dominated Internet services model represents severe endangerment to critical civil liberties such as privacy, freedom of information, and freedom of speech.
The existing proprietary regime leads to the wrong manner-of-existence for software and the wrong model for provision of Internet services. Wrong in that it allows control of the service by the provider, and exploitation of the user’s data, in a way that is detrimental and unknown to the user. The solution to this is an entirely different model for Internet services, where service ownership is placed squarely in the public domain.
4 The Libre-Halaal ByStar Digital Ecosystem
The Libre-Halaal ByStar Digital Ecosystem model is fundamentally different in every respect.
In terms of ownership, there is no ownership: Libre-Halaal Services in software form are a communal public resource, with no patent, copyright or secrecy barriers to free access and usage by anyone.
In terms of functionality, the software is open, so the services are completely transparent in operation. This transparency allows professional oversight by the engineering community, to verify the integrity of the service, ensuring that it in no way violates the interests of the user or the general public welfare.
And in terms of policy, operation of the service is governed by a social contract, drafted with full representation and advocacy for the individual user and the general public welfare.
The Libre model thus fully guarantees the critical civil liberties that are endangered under the proprietary model.
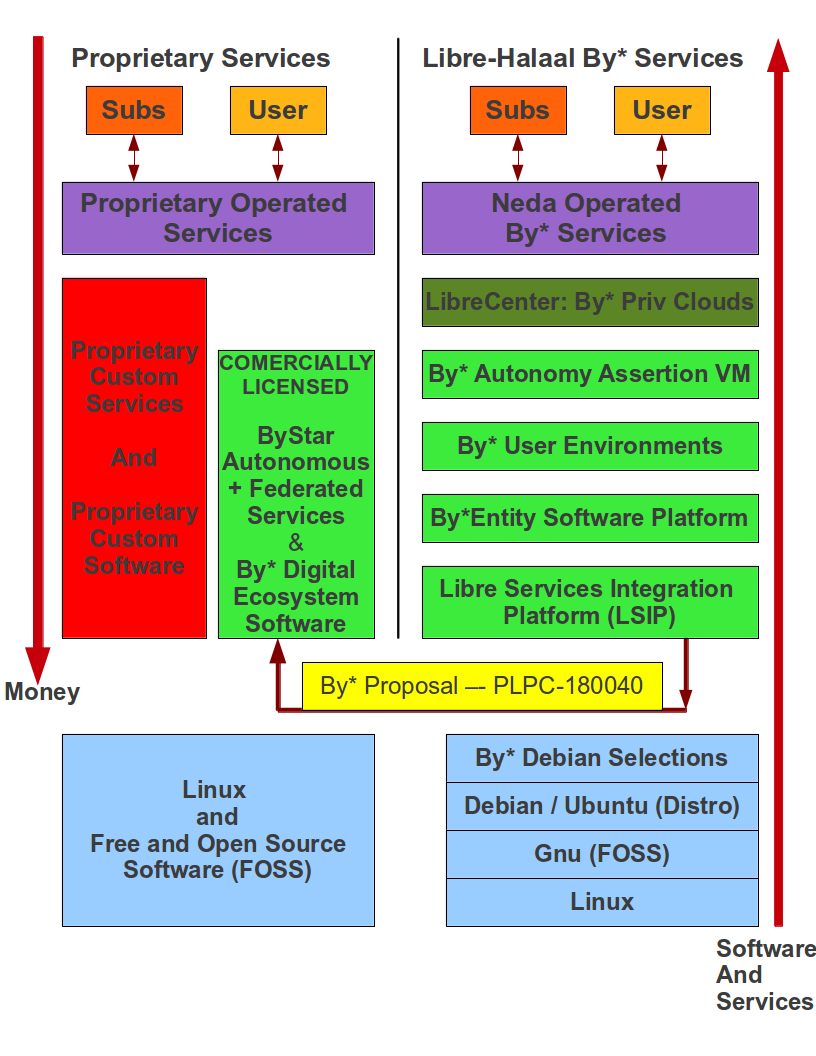
By* Federation of Autonomous Libre Services are Internet Application Services that are internally transparent and focus on preservation of user’s privacy and autonomy. By* stands against Facebook/Google/Yahoo/MSN/iCloud the same way that Linux stands against Microsoft Windows.
This is very different from existing Internet services capabilities. The Internet landscape of today has arisen in a highly disorganized, unstructured way, driven by a multitude of uncoordinated commercial ventures. The existing services capabilities have been built in a completely ad hoc manner, based on immediate business expedience, rather than any sort of coherent design. The result is the Internet Services industry as it appears today: a multiplicity of functionally isolated, incompatible services. And while this may not be apparent to the everyday user, having never experienced anything different, this limits the capabilities of Internet services in many ways.
By* is the model for a new generation of unified Internet services, far superior to the uncoordinated mishmash of services that exists today. It is designed for consistent, uniform interoperability across all types and manners of service usage. By* is the Internet services industry, done right.
We now present an overview of our work and the contours of ByStar in 4 regards – Ideology, Model, Capabilities and Economics.
4.1 ByStar Ideology: The Libre-Halaal Philosophy
|
Libre-Halaal Internet Services
Defining Halaal Manner-Of-Existence Internet Services (LibreServices.org) A non-proprietary model for delivery of Internet services PLPC-180045 |
|
Libre-Halaal Software
(HalaalSoftware.org)
Defining Halaal Manner-Of-Existence Of Software PLPC-180044 |
|
The Nature of Poly-Existentials:
Basis for Abolishment of The Western Intellectual Property Rights Regime PLPC-120033 |
|
Introducing Halaal and Haraam into Globish
Based on Moral Philosophy of Abstract Halaal PLPC-120039 |
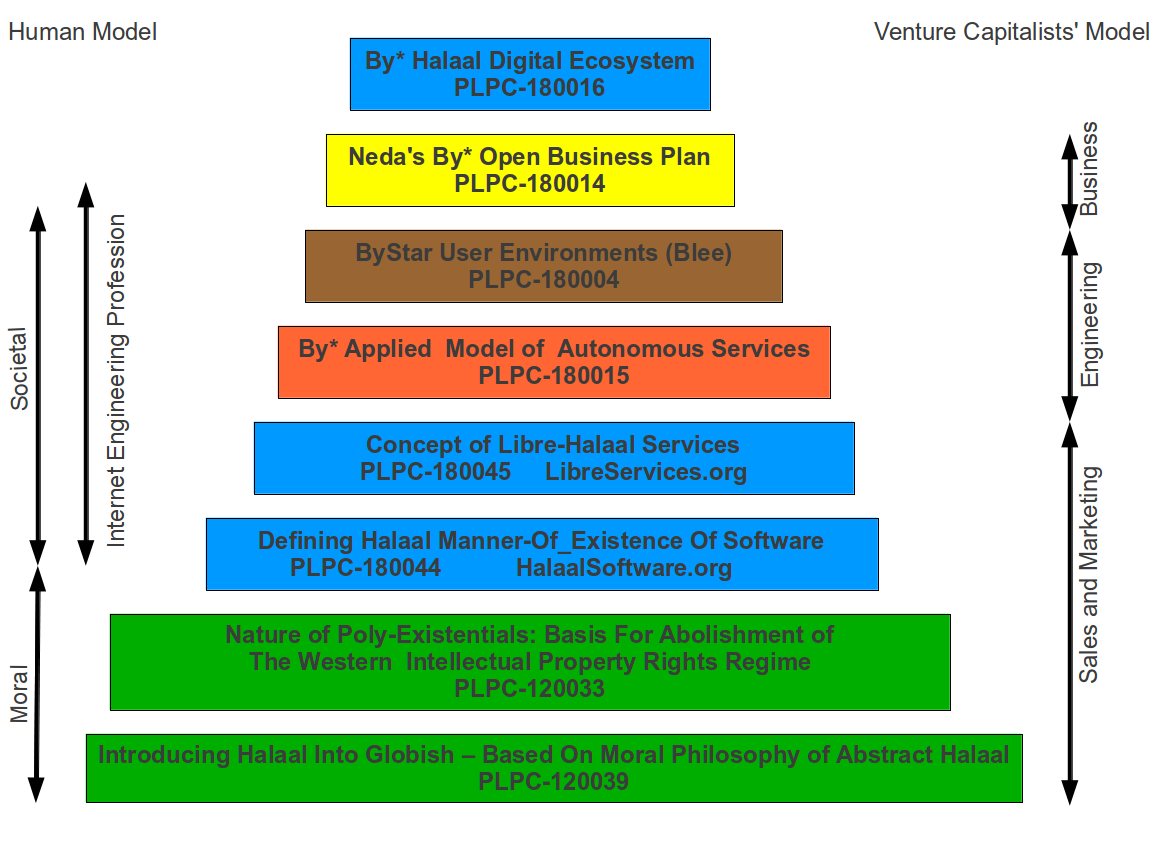
Figure 3: ByStar Ideology Documents Roadmap
A very important aspect of societal framework which has immediate impact on the shape of digital ecosystems are laws and models governing poly-existentials (knowledge, ideas, information, the digital entities). Societal Agreements governing all that is digital (and more broadly poly-existential) in the West is based on the IP regime. This has shaped the entirety of Western Digital Ecosystems.
In contrast, ByStar is ab-initio driven by the ideology that morality and health of society should be the foundation of the ByStar digital ecosystem. The fundamental difference between ByStar ideology and the Proprietary American ideology is that in ByStar priorities, society/humanity comes first and profit/economics come second. In the Proprietary American priorities profit/economics comes first and above all else.
In Figure 3, we present a roadmap in forms of layers. Each layer has a document that addresses that concept. Each layer builds on the layers below. At the lowest layer lies moral and societal questions of right and wrong (halaal and haraam).
The two green layers at the bottom are philosophical, moral and societal. Their scope is wider than the moral digital ecosystem that we are after. Generally speaking, they are not the domain of engineers. They are the domain of ethicists, philosophers and sociologists.
The blue layers are philosophical, moral, societal, social and engineering aspects of digital ecosystems that require direct involvement of engineers.
4.1.1 Halaal and Haraam and The Libre-Halaal Label
Our focus as engineers is to build the right thing.
We introduce the sensitive and potent word “Halaal.” We define this in the document titled:
Introducing Halaal and Haraam into Globish
Based on Moral Philosophy of Abstract Halaal
http://www.by-star.net/PLPC/120039 — [6]
We precisely define what we mean by “Halaal” and “Haraam” and the explicit context and scope of the “Libre-Halaal” label. We use the word Halaal carefully and consistently to emphasize that our work is anchored in morality.
Briefly, philosophical halaal is “manifestation” of “moral sensibilities” relevant to a specific topic where “the set of actions” map to “right.” And, philosophical haraam is “manifestation” of “moral sensibilities” relevant to a specific topic where “the set of actions” map to “wrong.”
We then focus on the halaal manner-of-existence of poly-existentials. There are things in nature that exist in singular and there are things that exist in multiples. That which exists in nature in singular, we call mono-existential. That which exists in nature in multiples, we call poly-existential.
Increased importance of role of poly-existentials (knowledge, ideas, information, the digital domain) in our lives and their impact on society and humanity now requires analysis towards recognition of halaal and haraam for different forms of poly-existentials. And once we have recognized the halaal manner-of-existence of poly-existentials we need to label it.
In the “Libre-Halaal” label, Libre indicates that:
- The scope of consideration of Halaal is manner-of-existence of poly-existentials.
- We reject the Western IPR regime. That the natural right to copy and the natural right to apply knowledge are the basis of our ideology.
Halaal indicates that:
- We are rooted in philosophy and morality — Not just economics.
- For each form of poly-existential, the manner-of-existence that permit Professions to safeguard society and humanity are the Halaal manner-of-existence for that poly-existential.
4.1.2 Guardianship Of Internet By The Engineering Profession
In ByStar ideology, it is the responsibility of the Internet engineering profession to preserve autonomy and privacy of the individual and health of social and societal interactions.
In order for the engineering profession to fulfill these responsibilities, certain societal agreements with respect to the manner-of-existence of software and Internet services need to be in place. We use the “Libre-Halaal” label to express the required societal agreements.
In the Proprietary American Ideology, there is no Internet engineering profession responsibility – engineers are instruments of business. Profit is the prime directive. As a result, manner-of-existence of software and Internet services is closed and restricted (proprietary), rooted the Western IPR Regime.
We draw a clear distinction between what Software Internet Engineering Profession means in the context of the Proprietary American Digital Ecosystem and what it means in the context of the Libre-Halaal ByStar Digital Ecosystem. In ByStar we use the term “profession” in the way it is understood in the East.
The notion of a “profession” in the West consists of training and the acquisition of specialized skills, to perform specialized work, to create monetary income. The responsibility of a profession towards society at large does not factor significantly in this. Western society is mostly, if not totally, economically driven. The Western model of economically driven individuals existing within an industrial context considers only money and self-interest. Such broader concepts as society, profession, responsibility and respect are very weak in the Western model.
In the East the word “profession” carries a greater meaning. It includes the Western meaning of a specialized skill set to perform work of value to others. But it also includes an agenda of trust and responsibility. The professional person is entrusted by society to maintain guardianship over an important aspect of life. Based on proper execution of this responsibility, the profession is respected.
The primary author of this essay, attests that: for him as an engineer it is only in Iran that he is called “Mr. Engineer Banan.” That has never happened to him in America, Canada, England, France, or anywhere else in his travels throughout the Western world. In return for all that respect, Mr. Engineer Banan owes the society something, doesn’t he?
So it is in this Eastern sense that we are here speaking of “professional responsibility.”
4.1.3 Nature Of Poly-Existentials: Basis For Abolishment Of Western IPR Regime
Central to our ideology and approach is full rejection of the Western so-called Intellectual Property Rights regime of copyright and patents.
In a document titled:
The Nature of Poly-Existentials:
Basis for Abolishment of The Western Intellectual Property Rights Regime
http://www.by-star.net/PLPC/120033 — [10]
We analyze and discredit the Western Intellectual Property Rights regime based on the inherent nature of what it seeks to control and restrict – poly-existentials: all that can be learned and remembered and all that is digital.
Poly-Existentials are poly-possessable. Assignment of restrictive ownership to what is poly-possessable is in conflict with nature.
The Western Intellectual Property ownership regime is in conflict with nature, it does not serve the ideal intended purpose of societal regulations, i.e. to balance rights equitably among conflicting constituencies. On the contrary, it has the effect of enriching a minority of powerful vested interests, to the very great detriment of society at large. The detrimental effects include the obstruction of engineering creativity, a distortion of the competitive business environment, and denial of the benefits thereof to the public.
Many societies fully reject the basic concept of patents and copyright. Yet, the Western Intellectual Property ownership regime is portrayed by Westerners as universal and global. Since poly-existence and digital entities are inherently not restricted by borders, the nature of global Internet demands rejection of the Western Intellectual Property ownership regime.
4.1.4 Libre-Halaal Software – Halaal Manner-Of-Existence Of Software
Next we focus on the correct manner-of-existence of software.
We do this in a document titled:
Libre-Halaal Software
Defining Halaal Manner-Of-Existence Of Software
http://www.by-star.net/PLPC/180044 — [8]
Our definitions for Halaal manner-of-existence of software and Internet service are concrete and precise. These definitions are similar to the “Free Software” and “Open Source” definitions but are distinct. As engineers, our legitimacy for addressing this topic is our responsibility to the engineering profession and the engineering profession’s responsibility to society.
We have created the http://www.HalaalSoftware.org site for further cultivation of the concept of Libre-Halaal Software.
Software (and more broadly Digital-Entities) is Libre-Halaal Software (and more broadly Libre-Halaal Digital-Entity) if it has the all of the following attributes:
- Halaal Criterion 1 – Unrestricted Multi-Possessibility. There are no restrictions is possessing the software by anyone who wishes to possess it – There are no restrictions in copying and redistributing copies.
- Halaal Criterion 2 – Unrestricted Usage. There are no restrictions for using (running) the software.
- Halaal Criterion 3 – Internal Transparency. The source code of the software is available to all software engineers to examine the software and study how it works. Unless software is internal transparent, the software can not be trusted.
- Halaal Criterion 4 – Modifiability. Software engineers must be able to modify the software, re-install the modified version and use the modified version without restrictions. The available source code of the software permits software engineers to change and enhancement it.
- Halaal Criterion 5 – Proper Authorship Attribution. The authorship of the software is not misrepresented.
Additionally, the software engineering profession requires from software engineers that the perpetuallity of all of the above be applied to all public modifications of the software. In other words, any modification or enhancement that is generally offered as software or service forever shall also have all of the above attributes.
4.1.5 Libre-Halaal Internet Services – Halaal Manner-Of-Existence Of Internet Services
We then introduce the concept of “Libre-Halaal Services” and describe the model for guaranteeing internal transparency of Internet application services in a collaborative environment.
In the document titled:
Libre-Halaal Internet Services:
Defining Halaal Manner-Of-Existence Of Internet Application Services
A non-proprietary model for delivery of Internet services
http://www.by-star.net/PLPC/180045 — [7]
We have formulated a radically new, non-proprietary model for delivery of Internet services.
Internet services are in essence access to remote execution of software. Fundamental Difference between software and service is Possessibility. Possession is personal and increases autonomy. Lack of possession decreases autonomy. Hence, software by nature is less of a threat than internet services are to autonomy.
Libre-Halaal Services are an extension of the principles of Libre-Halaal software into the Internet services domain. They are Internet services that can be freely copied and reused by anyone. The Libre Services model exists in relation to the proprietary Internet services model of Apple, MSN, Yahoo and Google, in an analogous way to how GNU/Linux exists in relation to Microsoft Windows.
We have created the http://www.LibreServices.org site for further cultivation of the concept of Libre-Halaal Services.
4.2 ByStar Applied Model Of Federations of Autonomous Libre-Halaal Services
In addition to being Libre-Halaal, ByStar is based on the Unified Autonomous model.
The Internet Services industry has arisen in a highly disorganized, unstructured way, driven by a multitude of uncoordinated commercial initiatives. The various industry capabilities have been built in an ad hoc manner, based on immediate business expedience, rather than by any sort of overarching engineering design. The result is the Internet Services industry as it exists today: chaotic, non-collaborative, uncoordinated, and falling far short of its true potential.
In contrast to this, the ByStar Digital Ecosystem is based on a coherent, collaborative, scalable, generalized Internet Services model.
Together, the Libre-Halaal Services and By* models have enormous implications. The Libre Services development model, and the By* unified services model, can transform the Internet completely, from the proprietary and ad hoc model of today into something far more powerful.
The realization of this potential is large, complex and ambitious. It is far too large in scope to be accomplished by any one company acting alone, but instead can only be accomplished as a coordinated industry-wide effort. But the ByStar Libre-Halaal Services model enables precisely the necessary large-scale, distributed, cooperative effort.
In the document titled:
The ByStar Applied Model
Of Federations of Autonomous Libre-Halaal Services
http://www.by-star.net/PLPC/180015 — [3]
We provide an overview of the model and design of ByStar Federation of Autonomous Services.
Based on this model and structures, ByStar services can consistently grow and interact with other ByStar services to provide a rich and healthy environment.
4.2.1 The ByStar Reference Model
ByStar is based on a set of key abstractions, representing the major real-world entities that must be represented within a generalized web structure. These entities include such things as individual persons, businesses, physical locations, and events. For each such entity we have defined the structures and conventions required to represent, instantiate and name that entity in a unified, consistent way, and at a very large scale. We have then defined the major classes of services required to manage these entities, and to allow highly generalized interactions within and among each other.
In the ByStar applied model, a real-world entity type (for example individuals or a physical locations) maps on to a ByStarEntityType (BxEntityType). A real-world entity instance maps on to a ByStarEntity (BxEntity) All ByStar services are anchored in ByStarEntity.
ByStarEntityTypes are structured hierarchically in a tree.
ByStarEntityType is either a ByStarAutonomousEntityType or a ByStarControlledEntityType.
ByStarAutonomousEntityType and ByStarControlledEntityType are either Classified or UnClassified.
In this structure, persons identified by their name, are represented as:
ByStarEntityType=ByStarAutonomousEntityType.Classified.Person.ByName
Each BxEntity (an instance) is identified by BxEntityId.
A BxEntityId is structured as:
BxEntityId=RegistrarId+BxEntityType+InstanceId
All ByStarEntityIds are unique. The InstanceId is assigned by the RegistrarId.
Each BxEntity can be activated within a
ByStarAutonomyAssertionVirtualMachine (BxAutonomyAssertionVirtualMachine).
The representation of a
BxEntity in a BxAutonomyAssertionVirtualMachine
is called a
ByStarServiceObject (BxServiceObject).
A ByStarServiceObject maps to a Unix account and
a user-id.
The BxServiceObject can have any
ByStarServiceCapability
that BxAutonomyAssertionVirtualMachine offers.
Currently, ByStarServiceCapability is one of the capabilities enumerated in figure 5.
Any ByStarServiceCapability can be bound to and exposed through a registered domain name.
Based on the above structures, ByStar services can consistently grow and interact with other ByStar services to provide a rich and healthy environment.
4.2.2 Domain Name Bindings Of ByStarEntity
Each ByStarEntity consists of specific information and a set of computing and communication services.
Publicly, BxEntity is usually exposed throughout Internet at a selected DNS domain name. In the ByStar model, binding of a BxEntity to one or more domain names is designed to be very flexible. This flexibility relates to Service Portability, but is broader. These notions are absent or very rare in the Proprietary American model.
For instance, in the context of the examples described in Section 5, Bob Smith is assigned BxEntityId=23.1.2.7.3.32674 which is canonically bound to the base domain name 5.bob.smith.byname.net.
ByStar permits Bob Smith to bind his BxEntity to other domain names, for example bobsmith.fr. In the ByStar BySMB service this is common place. Often, with the anticipation of obtaining example.com, example.bysmb.com and its BxEntity can be pre-generated. The owner, can re-adjust the binding of BxEntity to a chosen domain name at will.
Different information, different capabilities and different features of a BxEntity are usually bound to different domain names within a base domain name hierarchy.
For example, Bob’s imap service is at imap.5.bob.smith.byname.net, his genealogy service is at geneweb.5.bob.smith.byname.net and his synchronization repository (version control – vc) is at vc.5.bob.smith.byname.net.
In cases where the owner asserts autonomy by possession of the service as a BxAutonomyAssertionVirtualMachine, ByStar provides the ability to selectively DNS resolve BxEntity domains locally. This, then also permits fully local (non-networked) development and access to BxEntity – based on existing DNS bindings.
These flexible ByStar domain name to BxEntity bindings, and flexible DNS resolutions, are built on top of djbdns.
4.2.3 ByStar Autonomous Services
| (1) Software Transparancy -- Libre-Halaal Software | ||||
| Tangible | (2) Service Transparancy -- Libre-Halaal Services | |||
| (3) Service Possession Assertion -- (ByStar) | ||||
| Service | (4) Services Control -- (ByStar) | |||
|
|
||||
| Autonomy | (5) Service Portability -- (ByStar) | |||
| (6) Service & Information Non-Retention -- (ByStar) | ||||
Figure 4: Tangible Autonomy – ByStar Autonomy Assertion Virtual Machine
Internet services come in all shapes and sizes, serve all manner of purposes, and interact with each other and with societal entities in all manner of complex ways.
In some cases a service may be associated exclusively with a particular societal entity, such as an individual, an organization, or a corporation. Such entities enjoy a high degree of autonomy within society, and so we refer to these as autonomous entities. When a service is associated uniquely with particular autonomous entity, we refer to the entity as the owner of the service.
When a service is associated with a unique “owner”, certain characteristics of the service are of particular concern to the owner. The service may include information of a personal or private nature, and the owner may wish to ensure that his/her/its privacy is protected. It is also important that the service reflect and maintain the autonomy of the owner, providing parallel freedom of action to that which the owning entity enjoys at large.
Certainly, the privacy and autonomy of the owner are fully guaranteed if the owner exercises direct control over the functioning and provision of the service. In practice, an owner may or may not choose to exercise such direct control of the service. In many cases the owner of the service will leave the service provisioning in the hands of a second-party service provider. Nevertheless it is sufficient to guarantee the autonomy of the owner if the nature of the service is such that the owner could in principle take control of the service himself.
We define an autonomous libre-halaal service as an Internet service associated with a unique owner, that the owner could in principle and at his option take control over and provide for himself.
ByStar services are structured in two layers. (1) ByStar Autonomous Services and (2) ByStar Federated Services.
Any ByStar Autonomous Service may also include ByStar Controlled Services.
As noted, in many or most cases the service will be provided by a second-party service provider, who runs and administers the service on behalf of the owner. The autonomy of the owner requires that he is in no way tied to this or any other service provider. The general societal autonomy of the owner means that for any other type of service—banking, legal, medical—the owner is free to move from one provider to another, leaving no trace of himself behind with the previous provider.
In the case of Internet services, similar principles apply. For a service to be an autonomous halaal service, it must satisfy the twin requirements of portability, and non-retention. Portability, meaning the owner can transport the entire service to a different service provider. And non-retention, meaning the previous provider must retain no trace of the owner’s information.
Specifically, when a second-party provider is providing the service on behalf of the owner, the service is an autonomous halaal service if the provider meets the following requirements:
- Service and Data Portability. At the instruction of the service owner, the entire service can be transferred to a different service provider. This could be another second-party provider, or the service owner himself.
- Service and Data Non-Retention. At the instruction of the service owner, the service provider must destroy all service-related information (i.e. all owner data and log files).
4.2.4 ByStar Controlled Services – Internet Of Things
Any ByStar Autonomous Service may control certain “ByStar Controlled Services” that are his.
A ByStar Controlled Service is a ByStarEntity which is in control of ByStarAutonomousEntity.
As an example consider an individual (say the author – http://mohsen.1.banan.byname.net) who hypothetically owns a house, a bicycle, a Nike fuel band and a tag for his suitcase.
Virtual representation of these could be:
- A House – http://info.1-98008-5807-10.bywhere.net – where ByWhere structure links control to its owner (a ByStarAutonomousEntity).
- A Bicycle – whose location information goes to it owner (a ByStarAutonomousEntity) and not Google-corporation.
- A Nike Fuel Band – which send the exercise information to its owner-individual (not Nike-corporation).
- A tag for his suitcase – which links to it owner (a ByStarAutonomousEntity).
Each of these as a ByStarControlledEntity will be controlled by the ByStarAutonomousEntity. All of these are ByStarEntity-s. The ones that are controlled, link to their controller. The ByStarAutonomousEntity has links to all the ByStarControlledEntity-s that it controls.
So, we now have a framework for abstracting individuals as owners/controllers through ByStarAutonomousEntity. And we have abstractions for things to be owned and controlled through ByStarControlledEntity. And we have a framework for interaction of individuals/things and things/individuals through ByStar Federated Services.
Now, compare the model of ownership and interactions of Things in Libre-Halaal ByStar Digital Ecosystem – which is anchored in the autonomous individual – with the Proprietary American Digital Ecosystem – which is anchored in the Proprietary Corporation. There the proprietary internet service provider controls individuals also through Things.
4.2.5 ByStar Federated Services
Autonomous services and their controlled services may wish to engage in end-to-end interactions with other autonomous services. But in order to facilitate such interactions, involvement of some intermediary services may be needed.
We refer to such enabling intermediary services as federated services, and we refer to the association of a federated service plus its subscribing autonomous services as a federation of autonomous services.
The concept of Federated Services is layered above Autonomous Services and focuses on interactions amongst Autonomous Services and facilitation of information aggregation amongst ByStar Services.
An example of a federated service for information aggregation is ByTopic.org where autonomously published content (documents/music/video) is optionally centrally republished – autonomous and federated publication are fully consistent.
4.2.6 ByStar Convivial User Environments – Blee and BxGnome
Users experience ByStar Services through ByStar User Environments.
ByStar services can be accessed in a variety of ways. In addition to the traditional browser based model, ByStar provides for rich and deep Software-Service integration.
Initially we are focusing on two convivial, [5], User Environments for ByStar.
Blee (ByStar Libre Emacs Environment) is a layer above Emacs and Firefox that integrates ByStar platform (Debian GNU/Linux) capabilities into Emacs and provides for integration with ByStar Services.
An overview of this User Environment is provided in:
Blee and BxGnome:
ByStar Software-Service Continuum Based Convivial User Environments
http://www.by-star.net/PLPC/180004 — [11]
The deep integration between Libre-Halaal Software and Libre-Halaal Internet Services creates a Libre-Halaal Software-Service continuum, far superior in capability to any Proprietary/Haraam Software/Service combination.
4.2.7 ByStar Content Generation and Content Publication Facilities
ByStar offers a rich environment and a number of facilities for content generation.
Autonomous Content Publication facilities are a well established feature of ByStar.
In the document titled:
ByStar Content Production and Publication Facilities
http://www.by-star.net/PLPC/180038 — [13]
we describe capabilities and features of ByStar content generation facilities and ByStar autonomous content publication facilities.
Autonomous self publication can then be augmented by information aggregation federated services such as ByTopic, ByContent and BySearch.
4.3 ByStar Architecture Principles
The ByStar Digital Ecosystem is driven by a set of engineering architecture principles. We summarize some here.
4.3.1 Tools For Conviviality
Our primary criteria for software component selection and service design is “conviviality”.
By conviviality we refer to the concept of “Tools for Conviviality” as Ivan Illich introduced it.
In the document titled:
Introducing Convivial Into Globish
http://www.by-star.net/PLPC/120044
we introduce the concept of "Convivial" into Globish.
Briefly, in Illich’s words:
Tools are intrinsic to social relationships. An individual relates himself in action to his society through the use of tools that he actively masters, or by which he is passively acted upon.To the degree that he masters his tools, he can invest the world with his meaning; to the degree that he is mastered by his tools, the shape of the tool determines his own self-image. Convivial tools are those which give each person who uses them the greatest opportunity to enrich the environment with the fruits of his or her vision. Industrial tools deny this possibility to those who use them and they allow their designers to determine the meaning and expectations of others. Most tools today cannot be used in a convivial fashion.
The dynamics of the Proprietary American Digital Ecosystem are such that they produce industrial tools.
The Libre-Halaal ByStar Digital Ecosystem is designed to fully reside in the Libre-Halaal-Convivial quadrant, [8].
4.3.2 ByStar End-To-End Philosophy – vs Rise of the Middle
The dominant model of interaction between people and the model of access to information in the Proprietary American Digital Ecosystem is the centrally controlled Rise-of-the-Middle model – which puts the service provider at the center of all interactions so that it can exploit users and traffic information.
The ByStar model, in contrast, is end-to-end oriented and is based on the following principles:
- Make Services Autonomous Whenever Possible (peer-to-peer oriented)
- Invest and Focus on End-to-End communications facilities amongst Autonomous Libre Services
- When a Federated Service functions as an intermediary, limit its role to the bare essential of hooking the two ends. Thereafter, communications can be end-to-end.
4.3.3 Choice Of Software Components
The Libre-Halaal software model is a flourishing creative environment, generating a constant stream of new and better software packages, duplicating and surpassing the capabilities of an ever-increasing portion of proprietary software territory. Indeed for any particular item of functionality, there are typically multiple alternative free software packages available.
In this environment the model for implementation of By* service functionality is not one of original software development. Rather it is a process of intelligent selection and integration of functional components from the Libre-Halaal software creative environment.
So in creating By* our task has not been to write functional software components—in fact we have written almost none. Our main task has been to make careful engineering choices among the available free software components, and integrate these properly into the By* framework. In making these choices we consider not just the features and capabilities of each software component, but also the compatibility of the component within the overall By* architecture.
The main considerations in our choice of software components have been:
- Conviviality
- Scalability
- Libre-Halaal Mainstreamness
- ByStar Consistency
Virtually all the initial By* service functionality has been created this way. The following are some of the basic By* features that have been included by this process:
- Debian GNU/Linux.
- Base: djbdns, daemontools, ucspi, multilog, ...
- Mail: qmail, courier, spamassassin, ezmlm, ...
- Web: apache, zope, plone, geneweb, squirellmail, jquerymobile, galleria, ...
We will continue to select and incorporate additional software packages as these materialize within the free software environment. We will not create, so much as we will harvest. Or to paraphrase the common industry dictum: Good programmers write good software; great programmers reuse and integrate.
This is the extraordinary power, and magic, of free software: the ability to take things and reuse them at extremely low cost. This is what has allowed a small consulting company in Bellevue to create the beginnings of something that can eventually displace MSN and Google.
4.3.4 Confidentiality, Anonymity and Privacy
By confidentiality we mean: ensuring that information is accessible only to those authorized to have access.
By anonymity we mean: the characteristic of any interaction where an individual protects his or her identity from being shared with another person or with a third party in the context of particular communications.
By privacy we mean: the ability of an individual or group to seclude themselves or information about themselves and thereby reveal themselves selectively.
ByStar Autonomous Services are designed to provide tangible confidentiality, anonymity and privacy on large scale. All of Libre-Halaal ByStar Digital Ecosystem has this inherent design.
The basic assumption in the ByStar Digital Ecosystem is that all communications and traffic is subject to eavesdropping and traffic analysis.
Fortunately, the nature of digital information is such that it is easier to encrypt than it is to decrypt.
With nature on our side, ByStar Digital Ecosystem provides large scale countermeasures which include end-to-end data confidentiality and traffic flow confidentiality.
ByStar federated services are governed by transparency and well understood logging expectations and audit trail protections which are oriented towards preservation of privacy.
All of this is in stark contrast to how confidentiality, anonymity and privacy are in the American Proprietary Digital Ecosystem. There, they have become a currency.
4.4 ByStar Central
The basic design of ByStar is very distributed. Services are generally autonomous and interactions are usually end-to-end.
This means that ByStar is centrally light. But there are some fundamental and infrastructural and foundational organizations and services that are required at the center of ByStar.
The following infrastructure and foundational organizations have been put in place towards administration, guardianship, direction setting and facilitation of collaboration and growth of ByStar.
4.4.1 The Free Protocols Foundation – non-profit, non-proprietary
Free Protocols Foundation is the non-profit legal entity that facilitates collaborative development, maintenance and administration of ByStar.
4.4.2 Neda Communications, Inc. – for-profit, non-proprietary
Neda Communications, Inc. is the for-profit legal entity that has developed Libre-Halaal ByStar Services. The core of ByStar software is subject to the Affero v3 General Public License and also the Neda Commercial License (dual licensed). Neda plans to profit from widespread usage of The Libre-Halaal ByStar Digital Ecosystem in a variety of ways.
4.4.3 LibreCenter.net
LibreCenter.net is Neda’s data center. It is distinct and different from other data centers in that is built purely on Libre-Halaal Software. At this time most ByStar Services are hosted at Libre Center.
4.4.4 BySource.org
BySource.org is the Software Distribution Center for ByStar software in source form.
4.4.5 ByBinary.org
ByBinary.org is the Software Distribution Center for ByStar software in binary form.
4.4.6 ByStar Name and Number Assignment Authority
ByStar Name and Number Assignment Authority, is responsible for central assignment of names and numbers for ByStar services.
Design of ByStar as an ab initio independent separate digital ecosystem permits ByStar to expand beyond the Proprietary American Digital Ecosystem. This is desired and possible for two main reasons. First ByStar ideology may demand certain separations. Second, end-to-end purity of ByStar software-service continuum enables ByStar to do things that are not possible in the Proprietary American Digital Ecosystem.
ByStar’s Public Key Infrastructure (PKI) and the possibility of a ByStar Alternative DNS Root, and ByStar Digital Currency are some examples.
4.5 Current ByStar Services and Capabilities
| Foundational: |
ByStarEntityID
Shell Less Unix Account
PKCS Credentials Matched UE Profile Autonomy Assertion Virtual Box |
||||||
|
|
|||||||
| Personal Communication: | Email, Messaging, LibreTexting | ||||||
|
|
|||||||
| Web Features: |
Plone (CMS),
Galleries
Autonomous Self-Publication Genealogy, WebMail |
||||||
|
|
|||||||
| Private Network: |
Private Disk/Storage
Private Sync (Version Control)
ByStar Overlay Network Id |
||||||
Figure 5: Current ByStarEntity Instance Capabilities
ByStar Services are vast in scope. They are designed to be ever growing. Basic structures of ByStar is in place and many services are built or are partially built. The Libre-Halaal Services collaborative framework allows for ByStar to grow dynamically.
Thus far our focus has been in making sure that the overall architecture of the ByStar Digital Ecosystem is sound. We have been designing big and implementing gradually. A complete stable system is in place. It is now a matter of expanding and improving it.
In ByStar, today for email, we don’t use gmail, yahoo, msn, outlook.com, aol or other proprietary centrally controlled mail services. We use BystarMail. Similarly, for web presence, content publication, photo and video galleries ByStar has existing capabilities.
Here we provide a summary of where ByStar services stand today.
A snap shot of the organizations, services and software that form the ByStar Digital Ecosystem today are shown in Figure 7.
Free Protocols Foundation central resources are shown in violet in 7. Neda resources are shown in yellow. Current ByStarEntity generators are shown under the “ByStar Autonomous” label and ByStar federated services are shown next to them. ByStar software consists of three major layers, these are shown in blue.
The current status and growth of of ByStar falls into four broad categories:
- Current Capabilities of ByStarEntity (ByStarServiceObject) – what any autonomous services is capable of offering.
- Current Span of ByStarEntity Generators – What type of autonomous services (ByName, ByArtist, BySmb, etc) can be readily generated and supported?
- Current Scope of ByStar Federated Services.
- Scale of User Base – how many people are using ByStar?
Current capabilities of ByStarServiceObjects are enumerated in figure 5.
4.5.1 Current Capabilities of ByStarEntity (ByStarServiceObject)
Every ByStar autonomous service is anchored in a ByStarEntity. Every ByStarEntity can be provisioned to provide any of the current capabilities enumerated below.
- ByStarEntityIds and credentials – single password. [Unix account based]
- PKCS – ByStar Public Key Infrastructure (PKI) – Credentials.
- Autonomous VPN services and ByStar overlay networks. [openvpn based]
- Large amounts of autonomous disk space. [secure ftp based]
- Autonomous synchronization and version control facilities. [git – and also svn and cvs based]
- A Content Management System based website – with both public and private access. [Plone based]
- A conventional public web-site. [Apache based]
- Mobile web-sites. [jQuery Mobile based]
- Content publication services. [Plone based]
- A photo gallery. [galleria based]
- Genealogy web services. [geneweb based]
- Mail Transfer Service (MTA). [qmail based]
- Mail Access Service. [Secure Courier IMAP based]
- WebMail Service. [SquirrelMail based]
- Mailing List Services. [Ezmlm based]
- Mailing Distributions. [Gnus based]
- LibreTexting. [qmail and emsd based]
- Matched User Environment Profile. [Blee based]
Various other capabilities are in the works. With the ByStarEntity model in place, addition of features is quite simple.
4.5.2 Current ByStar Services Sites
| Federated | ByTopic | ByContent | BySource | BySearch | ByLookUp | ||
| By* Services | ByEvent | ByInteraction | ByHookUp | ByLeaks | ByBinary | ||
|
|
|||||||
| Controlled | ByFamily | ByWhere | ByMemory | ByEntity | |||
| By* Services | |||||||
|
|
|||||||
| Autonomous | BySMB | ByName | ByAlias | ByAnonymous | |||
| By* Services | ByAuthor | ByArtist | ByNumber | ||||
|
|
|||||||
| ByStar | By-Star | BySource | ByBinary | ||||
| Central | Neda | LibreCenter | Free Protocols | Libre Services | Halaal Software |
|
|
Figure 6: ByStar Domains Table
4.5.3 Current Status and Span of ByStarEntity Generators
A number of ByStarEntity Generators—the machinery required for fully automated creation of new service instantiations—are in place for a number of ByStarEntityTypes. Current ByStarEntity Generators are shown in Figure 7 under the “ByStar Autonomous” label. We thus have the ability to create unlimited numbers of new accounts in batch mode, or at any time we can “enable” the services, to permit self-service account creation by individual and business users.
4.5.4 Current Status and Scope of ByStar Federated Services
A number of sites are in place for facilitating inter-autonomous relations. Current Federated Services are shown in Figure 7 under the “ByStar Federated” label.
Our initial focus amongst federated service are those used for information aggregation. These include ByTopic, ByContent and BySearch.
4.5.5 Growth of user base: timing
An important consideration is the point at which we will begin to accept the burden of significant numbers of users.
In the case of a conventional service deployment there is typically a major emphasis placed on early and rapid growth of user base, to demonstrate demand and marketplace viability of the service, and lay claim to a particular portion of functional territory. This was modus operandi during the dot con era, where claims of user base numbers were an integral part of spin-and-flip and pump-and-dump model. Some of those attitudes still persist.
However we are not following this standard early proof-of-service approach. This may be appropriate for a conventional new service, where service functionality is the central and most critical issue. But for ByStar, a different timing strategy is required.
First, as a superset of numerous existing services, proof of service for By* in functional terms is already demonstrated by the Internet Services industry as it exists today. It is far more important to prove the model itself rather than its functional manifestations, and hasty creation of user base does little to accomplish this.
Instead we have provided a coherent and complete description of the model in this and our other documents. The theoretical basis for the model is solid, and this will be clear to anyone willing to invest the time to understand it. In addition a number of working By* implementations are already in place; examples are provided. Though the scale of usage remains small, these are sufficient to demonstrate the viability of the Libre-Halaal model and the ByStar design, and the value of the resulting services to paying clients.
But a far more important consideration is that installed base is very costly in terms of maintenance and support, and premature exposure to these costs can jeopardize the more critical work of building the underlying model machinery. Therefore we will not take on the burden of user base until the time and/or context is right for this. This means either that we are fully ready to accept the associated costs of ownership, or that the user base is being taken on in an appropriate context, such as a suitable business partnership.
Under either scenario our strategy is the same: at the right time we will populate the services at large scale by mass creation of By* service accounts for large existing user bases, [15].
Figure 7: Libre Services Supporting Organizations
4.6 Relationship With Existing Realities
The Libre Services and By* models are revolutionary, and can be expected to have a revolutionary effect on Internet usage. But these models are about service development and functionality, not about technological infrastructure. We are not reinventing the Internet protocols, or any other technical aspect of Internet operation.
What is being presented here is not a tear-down and rebuild operation.
Libre Services and By* imply no discontinuity, in terms of either technology or service deployment. The implementation model for Libre Services and By* is wholly evolutionary—there exists a continuous migration path from the proprietary model of today to the Libre model of tomorrow.
4.6.1 Relationship With The Proprietary American Digital Ecosystem
Based on ideology, the Libre-Halaal ByStar Digital Ecosystem fully avoids proprietary software and proprietary services. We simply avoid The Proprietary American Digital Ecosystem.
But, any and all of our services can be used in the Proprietary American model.
The core of ByStar software is subject to the Affero v3 General Public License and also the Neda Commercial License (dual licensed).
In a document titled:
A Strategy For Rapidly Becoming An Internet Application Service Provider
Joining, Adopting and/or Licensing ByStar
A Public Unsolicited Proposal
http://www.by-star.net/PLPC/180040 — [12]
We describe various options for those interested in joining, adopting and/or licensing ByStar.
4.6.2 Relationship With FOSS / FLOSS / FreedomBox Movements
Free and open-source software (F/OSS, FOSS) or free/libre/open-source software (FLOSS) is software that is both free and open source. It is liberally licensed to grant users the right to use, copy, study, change, and improve its design through the availability of its source code. In the context of free and open-source software, free refers to the freedom to copy and re-use the software, rather than to the price of the software.
Libre-Halaal ByStar Ideology and FOSS Ideology have a great deal in common and we closely collaborate with our FOSS brothers and sisters, but the ByStar Libre-Halaal Ideology is distinct.
We invite our “Free Software” and “Open-Source” brothers and sisters to recognize that the “Libre-Halaal Software” model is a more complete model and that the “Libre-Halaal Software” label is a better label.
4.6.3 Active Private Parallel Digital Ecosystems – Example: NSA
What we want to do on very large scale and in the open has been done in medium scale in private.
For instance, the United State’s National Security Agency (NSA) has created a separate parallel private digital ecosystem for its own use. NSA operates the private .nsa TLD; many NSA internal email addresses are of the form username@r21.r.nsa, mirroring the NSA organizational group structure. NSA has a particular ideology for its digital ecosystem which includes a large element of security, confidentiality and secrecy. NSA through use of its own particular software and services has created a complete different environment in parallel to the internet.
Precedence of such private parallel digital ecosystems combined with the proven power of Libre-Halaal software demonstrates that widespread realization of ByStar digital ecosystem is very viable.
4.6.4 Relationship With Piecemeal Privacy and Autonomy Software And Services
Some engineers kind of get it and have been trying to build various piecemeal privacy and autonomy software and services. Such efforts have always stayed limited in scope and scale. That is primarily for two reasons. First, because the engineers have failed to connect with society. And second, because piecemeal solutions don’t work.
We build on these piecemeal privacy and autonomy software and services and bring them into ByStar as integrated and complete large scale services.
An example of a piecemeal privacy effort is PGP - Pretty Good Privacy. A bunch of engineers and technologists use it amongst themselves but PGP never penetrated the society at large. ByStar comes with Public Key Infrastructure (PKI) as an integral part of the service and equivalent of PGP is an inherent part of ByStar.
Another example of a piecemeal privacy effort is Tor https://www.torproject.org. Tor attempts to accomplish traffic flow confidentiality just through redirection. Traffic flow confidentiality is an inherent part of ByStar which includes redirection and layer 3 and layer 7 padding as well.
4.7 ByStar Economics
|
The ByStar Economics Model:
The For-Profit and Non-Proprietary Quadrant An Inversion to the Proprietary Internet Services Model The Libre-Halaal ByStar Open Business Plan |
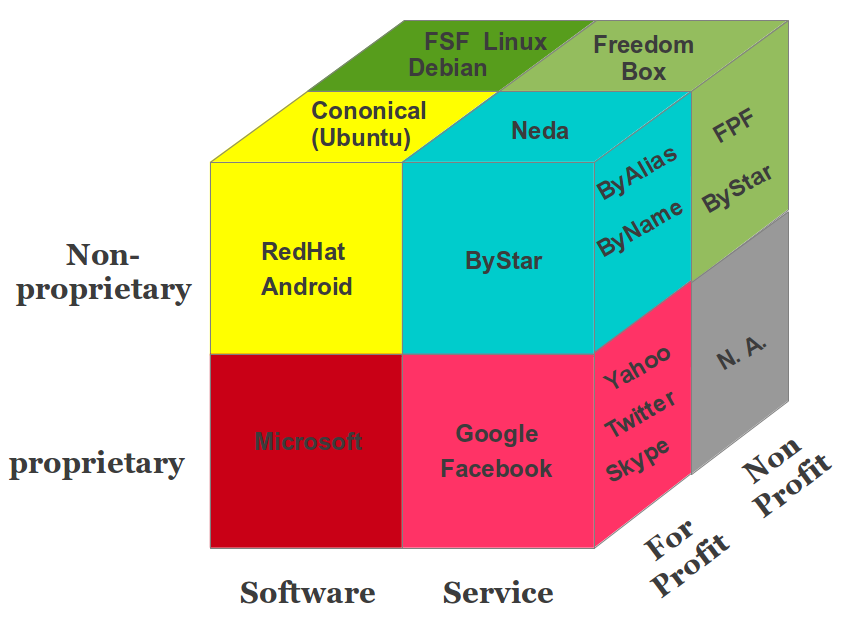
|
Figure 8: ByStar Economics Model
Having introduced the Libre-Halaal Bystar Digital Ecosystem in philosophical, moral, societal and engineering terms, we now turn our attention to the economic and business dimensions.
We are devout Capitalists.
The existing capitalist model for mono-existentials is generally correct, in both philosophical and economic terms. But the extension of the mono-existential capitalist model into the domain of poly-existentials, based on the Western IPR regime, is a grave mistake. Philosophically it is wrong. Societally it is harmful to humanity. And economically it is unstable and vulnerable, since it can be displaced by disruptive business models like ours. The ByStar Open Business Plan explains how this will come about, and how we will profit from this.
4.7.1 The For-Profit Non-Proprietary Quadrant
The notion of a non-proprietary construct, residing and operating within the for-profit sector, is new and different. Historically, the for-profit sector has been closely associated with proprietary ownership of assets. Hence the Internet Services industry as we see it today. Also historically, management of non-proprietary or public assets has been primarily associated with the non-profit sector. Hence the current orientation of the Free Software Movement, operating largely within the non-profit sector.
The Libre-Halaal Services deployment model breaks both these traditions. It represents a radical shift of the Internet Services industry from the for-profit, proprietary quadrant, to the for-profit, non-proprietary quadrant. In this space the entire software for an Internet service remains a communal public resource in the trust of the engineering profession, while service deployment is driven forward by the full force of for-profit commercial motivations.
In the document titled:
The For-Profit and Non-Proprietary Quadrant
http://www.by-star.net/PLPC/120042 — [4]
We provide more details on this topic.
As shown in Figure 8, the By* services are positioned in the For-Profit Non-Proprietary Quadrant For Internet Services.
As shown in Figure 8, the By* services are positioned in the For-Profit Non-Proprietary Quadrant For Internet Services. Note that in the non-proprietary layer, re-use and collaboration is far richer than the proprietary layer. For example, in the Software slice, Debian and Ubuntu cross progress. In the Services slice the same can happen. Where for example ByStar and FreedomBox can cross progress.
4.7.2 Revenue model for Libre-Halaal Software
The Libre-Haraam software model, operating under Western copyright restrictions, includes a highly effective recurring revenue generation model: the proprietary software licensing model.
But the Halaal manner of existence of software eliminates all restrictions on the distribution and use of software. Thus the Proprietary-Haraam recurring revenue model is also largely eliminated. Recurring revenues under the Libre-Halaal software model are much less than under the Haraam software model.
4.7.3 Revenue model for Libre-Halaal Internet Services
The Halaal manner of existence of software creates a powerful generative development model for Libre-Halaal Internet Services. This generative model is absent from Proprietary-Haraam Internet Services. Thus Libre-Halaal Internet Services have a major advantage and can compete directly with Proprietary-Haraam Internet Services in terms of development.
The basic recurring revenue models for Libre-Halaal Internet Service providers are essentially the same as for Proprietary-Haraam Internet Service providers. Thus in terms of revenue generation, Libre-Halaal and Proprietary-Haraam services are on an equal footing.
4.7.4 ByStar Value Chain Analysis
ByStar value chain is a chain of activities that we perform in order to deliver a valuable Internet services to the market. It is a high-level model of how we take raw externally developed Libre-Halaal software as input, add value to these software packages through various processes, and sell finished services to our customers.
In Figure 9, we illustrate the ByStar value chain on the left column and its inter-mixing with proprietary value chains on the right column.
Figure 9: ByStar Supply Chain Model
Focusing on the right column of Figure 9, notice that “Neda Operated By* Services” establish a direct relationship with Subscribers and Users at the very top. Note that the scope of these Internet services is everything – the * in By* – and that the intended scale of these services is planet-wide. By definition, no Internet services opportunity can be bigger than that.
The arrows between Neda Services and User/Subscriber in Figure 9 include an element of “Trust, Loyalty, and Respect” which is the result of “ByStar Ideology” that we presented earlier. The element of trust and respect is fully absent in the left column. In business terms, Trust and Respect, translate into “stickiness” – where the user is more committed to the service. So, you see, all our investments in ideology are actually also business wise.
All of the ByStar value chain software is Libre-Halaal (Free and Open Source) software. ByStar software in Figure 9 is shown in two different colors.
The software in bright blue represents Debian and/or Ubuntu GNU/Linux and the specific software packages that we have chosen. These are externally developed open source software packages which are typically subject to the free software GPL license (or similar) which permits their inclusion in proprietary services. This is often referred to as ASP loophole.
The software in bright green is the software that Neda has developed. It is subject to the “Affero General Public License Version 3” (AGPL3) and Neda Commercial License (Dual Licensed). AGPL3 closes the ASP loophole. Any ASP which uses ByStar software must subject its changes and improvements to AGPL3 and make its changes and improvements publicly available. Those ASPs not wishing to do so, can use ByStar software through the Neda Commercial License.
In the left column of Figure 9, we illustrate a typical proprietary ASP who is incorporating ByStar as part of its services based on the Neda Commercial License.
In this environment the model for implementation of By* service functionality is not one of original software development. Rather it is a matter of selection and integration of already available software packages. Virtually all existing By* service functionality has been created this way—in building By* we have written almost no new software components at all.
Thus we are not so much in the business of software development, as we are in the business of software integration. But the integration of software components to produce a coherent service is far from trivial. We have created a sophisticated technical integration environment for this purpose, called the Neda Libre Services Integration Platform (Neda-LSIP) [1].
Design of LSIP and the ByStarEntity Software Platform recognize the evolution of underlying external software (bright blue) in the ByStar value chain.bywhere This is the extraordinary magic of Libre-Halaal software and services: the ability to take things and reuse them at extremely low cost. This is the fundamental growth dynamic of Libre Services, and the powerful generative force that is lacking in the proprietary model. This is the key dynamic that causes the By* Libre Services eventually to surpass the proprietary model entirely in terms of features and functionality.
4.7.5 ByStar Open Business Plan
The halaal manner-of-existence of software creates a powerful generative development model for Halaal Internet Services. This generative model is absent from Proprietary/Haraam Internet Services. Thus Libre-Halaal Internet Services have a major advantage and can compete directly with Proprietary/Haraam Internet Services in terms of development.
The basic recurring revenue models for Libre-Halaal Internet Service providers are essentially the same as for Proprietary/Haraam Internet Service providers. Thus in terms of revenue generation, Halaal and Haraam services are on an equal footing.
As part of our responsibility to create a viable implementation construct we have fully analyzed the business dimension, and we have formulated the business model in the form of an Open Business Plan, titled:
The Libre-Halaal ByStar Open Business Plan
An Inversion to the Proprietary Internet Services Model
Neda Communication Inc.’s Open Business Plan
http://www.by-star.net/PLPC/180014 — [14]
http://www.neda.com/strategicVision/businessPlan
ByStar open business plan is available in 3 forms; the Condensed Summary (about 12 pages), the Executive Summary (about 15 additional pages) and the full plan (about 85 pages).
Our business plan is viable because we understand the critical dynamics of poly-existentials. The current direction of the Internet services industry does indeed present a grave hazard to humanity, and we will indeed safeguard humanity against this. These extraordinary claims provide a unique and powerful marketing message. And they also happen to be true.
4.8 Understanding The Full ByStar Picture
We have given you a brief summary of ByStar above.
This summary is over simplified and captures the gist of a series of articles that we have developed to analyze and describe various aspects of ByStar.
|
The Libre-Halaal ByStar Digital Ecosystem
A Unified and Non-Proprietary Model For Autonomous Internet Services A Moral Alterantive To The Proprietary Digital Ecosystem PLPC-180016 |
|
Neda's ByStar Open Business Plan
(neda.com)
An Inversion to the Proprietary Internet Services Model PLPC-180014 |
|
Blee and BxGnome
PLPC-180004
ByStar Software-Service Continuum Based Convivial User Environments |
|
The ByStar Applied Model
(by-star.net)
Of Federations of Autonomous Libre-Halaal Services PLPC-180015 |
|
Libre-Halaal Services
(LibreServices.org)
Defining Halaal Manner-Of-Existence Internet Services PLPC-180045 A non-proprietary model for delivery of Internet services |
|
Libre-Halaal Software
(HalaalSoftware.org)
Defining Halaal Manner-Of-Existence Of Software PLPC-180044 |
|
The Nature of Poly-Existentials:
Basis for Abolishment of The Western Intellectual Property Rights Regime PLPC-120033 |
|
Introducing Halaal and Haraam into Globish
Based on Moral Philosophy of Abstract Halaal PLPC-120039 |
Figure 10: The Libre-Halaal ByStar Digital Ecosystem Roadmap
In ByStar Publications List – http://www.by-star.net/bxPublications – we provide pointers to ByStar related articles. These documents evolve as ByStar evolves, and the publications list will be kept up-to-date. The ByStar publications list is structured primarily for reference. Below we provide a description of how these documents collectively draw a comprehensive picture.
The big ByStar picture is shown in Figure 10. Each of the layers in this figure represents either a conceptual definition (shown in blue), or an actual software/service implementation (shown in orange). Each layer builds on the layers beneath.
The layers in Figure 11 are color coded. Each of the layers are either:
- A Conceptual Layer.
- Representing concepts. Layers 1,2,3,4,7 and 8 are in Green, Blue and Yellow.
- A Tangible Layer.
- Representing software/service implementations. Layers 5 and 6 are in Orange and Brown.
The tangible layers are bound by the conceptual layers underneath them and receive legitimacy from those concepts.
The conceptual layers are validated by the tangible layers.
The green layers (1 and 2) at the bottom are philosophical, moral and societal. Their scope is wider than the moral digital ecosystem that we are after. Generally speaking, these are not the domain of engineers. They are the domain of ethicists, philosophers and sociologists.
The blue layers (3, 4 and 8) are philosophical, moral, societal, social and engineering aspects of digital ecosystems that require direct involvement of engineers and the engineering profession. The yellow layer (7) addresses economics and business dimensions of ByStar.
The orange/brown layers (5 and 6) are engineering constructs. They are in-use software and in-use Internet application services.
In ByStar Roadmap:
http://www.by-star.net/bxRoadmap
we provide a reading roadmap to ByStar related articles.
Figure 11 shows how the moral, legal, societal, engineering, economic and business dimensions of the ByStar Halaal Digital Ecosystem are layered as described above.
Note the differing characterizations of this layering on the left and right. Both characterizations are valid, but they reflect entirely different viewpoints. The left side characterization is called “The Human Model,” and reflects the philosophical, moral and societal elements of the model. It also identifies the role of the engineering profession in maintaining these elements. The right side characterization is called “The Venture Capitalist Model,” and is very different from the “The Human Model.” The same elements are present, but now represent their significance as part of an investment strategy. Thus the moral and societal concerns within the human model are now viewed as a sales and marketing opportunity. This makes clear that when dealing with Venture Capitalists, issues of morality and societal welfare are not the topic of discussion. In this regard Venture Capitalists need only understand that human beings are in fact concerned with vital moral considerations such as “privacy” and “autonomy,” and that these considerations have powerful sales and marketing consequences. And that our unconventional strategy of overturning their sacred-cow – Copyright and Patent model – gives us a huge competitive advantage.
Figure 11: Reading Roadmap For The Libre-Halaal ByStar Digital Ecosystem
The gigantic picture we have drawn in Figure 11 is a blueprint. It represents a complete framework for collaborative work towards an alternative to the current proprietary digital ecosystem. By aligning ourselves with the natural forces and dynamics of poly-existentials, and by means of large-scale unrestricted collaboration, we can achieve this.
5 ByStarEntity Realization Models – By Way Of Some Examples
Let’s explore ByStar in the context of a few examples. All these examples are completely fictional.
Let’s consider Bob Smith, a 46 year old university researcher and his 15 year old daughter, Alice Smith. Alice is a freshman (9th grader) at Garfield High School (GHS).
Bob wishes to have the following in ByStar.
- An Autonomous ByName BxEntity for his private and public use – 5.bob.smith.byname.net (he is the 5th bob.smith requesting byname services).
- An Autonomous ByFamily BxEntity for his family – 8.smith.byfamily.net.
- A Controlled ByFamily BxEntity for his daughter Alice – alice.8.smith.byfamily.net (Alice is a minor and Bob wishes to have the option of overseeing her communications).
- A Controlled ByWhere BxEntity for their condo in Kirkland, WA – 1-98034-3681-74.bywhere.net (say for reliable driving directions).
There are 3 different realization models for Autonomous BxEntity-s.
- Shared Cloud Autonomous Model
- Hosted Private Cloud Autonomous Model
- Premise Private Cloud Autonomous Model
Bob is concerned about privacy and prefers the “Hosted Private Cloud Autonomous Model” over the “Shared Cloud Autonomous Model”. He trusts the ByStar model enough not to need the “Premise Private Cloud Autonomous Model”.
In the following sections we describe ByStarEntity realization models in the context of Bob and Alice’s example.
As we go through these examples, we will also be comparing them with their counter part in the Proprietary American Digital Ecosystem.
5.1 ByStarEntityId Registrations
Through ByStar, Bob needs to have an Autonomous ByName Registration, an Autonomous ByFamily Registration and a Controlled ByWhere Registration.
So, Bob goes to http://www.byname.net and provides his name “Bob” “Smith” and an email address and agrees to conform to ByStar usage policies and in return, he receives:
- 5.bob.smith.byname.net – BxEntityId=23. 1.2.7.3 .32674 – BxEntityIdPassword=
Similarly Bob goes to http://www.byfamily.net and provides his autonomous BxEntityId=23.1.2.7.3.32674 and gets:
- 8.smith.byfamily.net – BxEntityId=23. 1.2.9.5 .4689
He then provides his autonomous BxEntityId=23.1.2.7.3.32674 and gets:
- 1-98034-3681-74.bywhere.net – BxEntityId=27. 2.2.6.4 .4689
for a ByWhere controlled entity.
All of the above were external registrations. In the ByStar model, Bob himself has now become a registrar for some ByStarEntitys.
Under the 8.smith.byfamily.net domain, Bob now registers
- bob.8.smith.byfamily.net – as BxEntityId=23. 1.2.9.5 .4689 .1
And
- alice.8.smith.byfamily.net – as BxEntityId=23. 1.2.9.5 .4689 .2
Note that Bob has the option of using a single password and that all his ByStarEntityId are related.
With his 5 ByStarEntityIds in place, Bob now can realize his ByStarEntitys in the model that he wishes.
5.2 Shared Cloud Autonomous Model
This model is very similar to how Gmail and other proprietary Internet services works. It involves Bob going to http://www.byname.net, logging in and using the web service.
Even at this level, there is a big difference between the Proprietary American Services and the Libre-Halaal ByStar Services. ByStar is transparent – not opaque/dark/closed.
Even in the shared cloud autonomous model, Bob has the choice of demanding that his entire service be delivered to him as a ByStarAutonomyAssertionVirtualMachine – that means the entire software for the ByStar service and his entire data be delivered to him. And that the service provider abide by the “Service Data Portability” and “Service and Data Non-Retention” obligations.
In the Gmail (and other) Proprietary American Model there are no such concepts.
5.3 Hosted Private Cloud Autonomous Model
5.3.1 Obtaining A Generic ByStarAutonomyAssertionVirtualMachine
Bob downloads to his laptop the latest generic ByStarAutonomyAssertionVirtualMachine. This has all the relevant software for ByStar services.
The latest generic ByStarAutonomyAssertionVirtualMachine is available at http://www.bybinary.org.
5.3.2 Adding ByStarEntitys To The Generic ByStarAutonomyAssertionVirtualMachine
Bob then adds his ByStarEntitys to the ByStarAutonomyAssertionVirtualMachine.
This involves Bob running the ByStarAutonomyAssertionVirtualMachine on his laptop and entering his ByStarEntityIds into the ByStarAutonomyAssertionVirtualMachine. All of Bob’s ByStar services are now added to his ByStarAutonomyAssertionVirtualMachine.
5.3.3 Choosing A ByStar Private Cloud Provider – e.g. LibreCenter.net
Bob then chooses a host for his Virtual Machine.
His choice of ByStar Private Cloud Provider may be influenced by the location and laws of where the ByStar Private Cloud Provider operates in. If U.S. wiretap laws are too invasive to his taste, he may choose a ByStar Private Cloud Provider outside of the U.S. – ByStar is very global.
Let’s say that Bob chose http://www.librecenter.net.
5.3.4 Running Your ByStarAutonomyAssertionVirtualMachine
Bob then transfers his fully configured ByStarAutonomyAssertionVirtualMachine to http://www.librecenter.net and runs the service.
Bob is now in control of his own service.
ByStar and LibreCenter have given Bob what is necessary and are supporting him. Bob is in possession of all of the service’s software and the service is Bob’s.
5.4 Premise Private Cloud Autonomous Model
In the Premise Private Cloud Autonomous Model, Bob is in possession and control of the entire software and the entire hardware for the service.
5.4.1 Obtaining A Premise ByStar Host
A Premise ByStar Host is a computer with a static public IP address capable of running a ByStarAutonomyAssertionVirtualMachine. Any modern desktop or laptop would do just fine.
5.4.2 Preparing The ByStarAutonomyAssertionVirtualMachine
Bob does what was previously described in Section 5.3.1 and Section 5.3.2 to prepare his ByStarAutonomyAssertionVirtualMachine.
A typical ByStarAutonomyAssertionVirtualMachine is capable of containing 100s of ByStarEntitys.
5.4.3 Running The Premise ByStarAutonomyAssertionVirtualMachine
Bob then puts his ByStarAutonomyAssertionVirtualMachine on his “Premise ByStar Host” and runs it.
Bob now possesses all of the software for ByStar.
Bob now possesses all of his own data.
Bob now possesses all of his logs and audit trails.
Bob now controls all of his services.
This means real and tangible autonomy.
Efforts like FreedomBox have been attempting to accomplish this in a more limited fashion. But in the ByStar model the Premise Private Cloud Autonomous Model is just one of many ways to realize tangible autonomy.
5.5 ByStar Autonomous Services Use and Access Examples
So, now Bob and Alice have a number of autonomous services in place. Now, let’s see how they will be accessing them and what these ByStar Autonomous Services can do for Bob and Alice.
5.5.1 Browser Based Web Service Usage
Most ByStar services are also offered as interactive web services just like traditional web services.
The generic ByStarAutonomyAssertionVirtualMachine includes all ByStar user environments. A Tor-Firefox browser is all you need for ByStar interactive web services.
But the prefered model for accessing ByStar services is through Blee.
5.5.2 Blee Based Software-Service Continuum Usage
Blee (ByStar Libre Emacs Environment) is a layer above Emacs and Firefox that integrates ByStar platform (Debian GNU/Linux) capabilities into Emacs and provides for integration with ByStar Services.
Use of Blee makes for a very rich software-service continuum model that does not have a real counter-part in the Proprietary American Digital Ecosystem.
5.6 Some Examples Of ByStar Autonomous Services Capabilities
With everything in place, let’s see what are some of their ByStar capabilities. ByStar full set of Autonomous capabilities is determined by the capabilities of Bob’s ByStarAutonomyAssertionVirtualMachine. These are already quite powerful and they are ever growing. Below we mention some.
5.6.1 ByStar Email (Messaging)
In terms of email capabilities, ByStar email is similar to Gmail. However, ByStar email is very autonomous, very personal and very private.
For example, note that email communications between Bob and Alice need not even leave Bob’s ByStarAutonomyAssertionVirtualMachine.
Beyond Gmail like capabilities, ByStar email service is inherently multi-address and multi-mailbox.
For example Bob and Alice can each have a specific address for Alice’s school – Garfield High School (GHS). Those email addresses would be:
- ghs@alice.8.smith.byfamily.net
- ghs@bob.8.smith.byfamily.net
Libre-Halaal ByStar email services are superior to Proprietary-Haraam email services both in capability and privacy.
5.6.2 ByStar Public and Private Web Presence Services
ByStar public and private web presence services are very rich. They are based on the Plone Content Management System.
The URL for Bob’s public web site would be http://5.bob.smith.byname.net. Its capabilities could be similar to the author of this document’s site: http://mohsen.1.banan.byname.net.
5.6.3 ByStar Photo and Video Galleries
Bob and Alice and their family’s (8.smith.byfamily.net) photo gallery can be similar to what is in: http://mohsen.1.banan.byname.net/albums.
ByStar Photo and Video Galleries are based on galleria and are integrated into Plone. ByStar photo gallery capabilities comfortably compete with the likes of flickr and photo bucket. The difference of course is that Bob and Alice remain in control of their photos with ByStar.
5.6.4 ByStar Genealogy Services
Bob and Alice can build their genealogy tree in ways similar to what is in: http://mohsen.1.banan.byname.net/genealogy.
ByStar Genealogy Services are based on geneweb. ByStar genealogy capabilities comfortably compete with the likes of ancestry.com, FamilySearch, and MyTrees.com.
The difference of course is that with ByStar, Bob and Alice remain in control of their genealogy personal information.
5.6.5 ByStar Libre Content Self-Publication Services
Bob Smith is an academic. He writes and publishes a lot. Some of his thoughts and writings are outside of the mainstream. As a true academic, he prefers not to subject his publications to restrictions that the likes of IEEE and ACM demand. His publication philosophy is consistent with ByStar Publication Philosophy.
He uses the ByStar Content Production and Content Publication Facilities to write and publish.
The list of his publications is similar to what is in:
http://mohsen.1.banan.byname.net/publications/collections/bystarDE.
The access page to Bob’s documents are similar to this document’s: http://mohsen.1.banan.byname.net/PLPC/180016.
Bob, can optionally use ByStar Federated Services to achieve permanence and ease of search and access to his writings. See Section 5.7 for more details.
So, ByStar has empowered Bob to be a true academic and avoid pseudo academic copyright-ed publication traditions.
5.7 ByStar Federated Services Examples
Bob has chosen to subject some of his publications to “Federated
Re-Publication”.
He uses http://www.bycontent.net for that.
ByContent is a ByStar Federated Service where ByStar self-published documents are republished.
By submitting some of his documents and podcasts (videos) for ByContent re-publication, Bob accomplishes several things.
ByContent Federated Services offer the following:
- Permanence. If Bob’s web site or he, himself disappear, his documents still remain.
- Large volume publication. ByContent runs on large computers with access to lots of bandwidth. Bob need not worry about slowness of access to his public videos and public writings.
- ByContent republication maintains reference to original source.
- Classification with peer content. Bob’s content is classified and sits next to other similar and competing content.
- Searchability. Bob’s content are now subject to search features of http://www.BySearch.org
ByContent is similar to YouTube. Except that ByContent allows your content to be clearly refered back to you. All of ByContent is copyleft.
5.8 Bob And Alice’s ByStar Digital Ecosystem
Now, Let’s look at this example in its entirety and see what Bob and Alice gained by buying into the ByStar Digital Ecosystem.
First, they lost nothing. ByStar exists in parallel to the proprietary Internet. Everything that everybody else can do, Bob and Alice can do as well. Through peer pressure Alice will likely be pushed to join Facebook.
But, Bob and Alice now have autonomous and private email. They communicate with everybody else in normal email fashion. But they are in control of their personal messages. When Bob deletes an email he knows that the email has truly been deleted.
And Bob and Alice are truly in control of what they do with their photos, and their content on the Internet.
That can be considered a good begining. ByStar is evolutionary. ByStar is designed to be ever-growing and comprehensive.
Are you ready to follow Bob and Alice’s example?
6 Dynamics of the Libre-Halaal vs. Proprietary-Haraam Battle
Though it is not part of popular cultural awareness, there is currently a titanic battle taking place between two competing ideologies: the proprietary software model (exemplified by Windows), and the libre-halaal software model (exemplified by GNU/Linux). This is a to-the-death battle, from which there can eventually emerge only a single winner.
The software battle is part of a broader ideological contest, about ownership models for poly-existentials in general (software, but also including literature, music, images, movies, etc.) in the digital era. This ideological war is rooted in the manner-of-existence of digital entities as this has broader ramifications for individuals and society – which impact autonomy, privacy, freedom, and social interaction.
The inherent nature of software, Internet services and other poly-existentials is fundamentally at odds with these historical conventions of physical property (mono-existentials) ownership. Such constructs have the inherent potential for unlimited replicability and dissemination, and in the age of the Internet this potential is now fully realized.
As a result the existing western Intellectual Property conventions are coming under increasing stress, as the internal forces of replicability clash with the externally constraining Intellectual Property framework. The Intellectual Property regime is also coming under formal intellectual attack, as the dysfunctionality and true costs of this regime become increasingly apparent.
In practice, the proprietary software and services model has engaged in various forms of bastardization of libre-halaal software model. Well recognized examples of such bastardizations include the service loophole, Tivoization, Appleization, and Androidization.
In practice, open-source and free software movements represent compromising models and ideologies. For the most part they are comfortable being intertwined with the proprietary model. Full rejection of the proprietary model is considered radical in much of the open-source culture.
In practice, with ByStar ideology we accomplish three things. First, we create a completely separate and independent digital ecosystem that fully rejects the proprietary model. Second, we take all possible measures to prevent bastardization of ByStar software and services by the proprietary model. Third, we create a comprehensive internet services business model which competes directly with the proprietary model in terms of revenue and profit.
6.1 Engineering vs. Business
Today, the Internet services industry is owned entirely by business interests. But the Libre Services and By* initiatives represent a startling challenge to this: they represent a determined reassertion of proper guardianship of the Internet by Engineering. This challenge will bring us into massive conflict with existing commercial interests, who will fight ferociously to defend the status quo.
Table 1 shows the many elements of contrast between the Engineering and Business value systems. As the table makes clear, these two values systems are in complete and total conflict. We will fully exploit this conflict as the metaphor of a war: a war between Engineering and Business, in which Business represents exploitation of the Internet for profit, and Engineering represents guardianship of the Internet on behalf of the public.
Proprietary vs Libre Libre Digital Ecosystem Proprietary Digital Ecosystem Laws, Values Patent-free Patented and Model Copyleft Copyright Software and Transparency Secrecy User Env Public ownership Private ownership Internet Services Sharing, collaboration this-is-mine-and-you-can’t-have-it Content Guardianship Exploitation
Table 1: Engineering vs. Business Polarization
6.2 War Of Ideas – War Of Words
ByStar is huge and powerful and viable. But given the entrenched vested interests in opposition to it, the promotion of ByStar amounts to a kind of war. ByStar has the inherent characteristics to prevail in this war – we have moral superiority, intellectual correctness, and a construct that is viable in every respect: technological, economic, societal etc. But it is essential that all this be communicated effectively.
The ByStar Wars (to coin a phrase) will be fought on multiple fronts. But as a revolutionary movement, to a significant extent it will be fought as a war of words and ideas. This means that the movement is advanced effectively in words, defended against attack in words, and extremely forceful and effective counter-attack made against its detractors.
Please refer to http://www.by-star.net/bxPublications for a list of publications that we have felt is necessary for ByStar to be equipped with.
6.3 Tear Points Of Libre-Halaal and The Proprietary-Haraam Tussle
We have analyzed the forces in nature that work against the existing Proprietary American Digital Ecosystem – and those which are in harmony with the Libre-Halaal ByStar Digital Ecosystem – and have identified a number of “tear points”. Our execution is focused on these tear points.
For ByStar to become truly widespread – a major realty at societal level – ByStar ideology needs to resonate with societal values. As such, on large scale, ByStar will likely be adopted in different societies to different extents.
Some of these tear points are more applicable to Eastern societies and some are more applicable to Western societies.
We present and analyze these tear points in the context of formulation of national policies for Eastern and Western societies.
6.4 Libre-Halaal Software Based Formulation Of National Policies In Western Societies
While America leads Internet technology today, full adoption of ByStar based on ByStar ideology will likely be difficult in America.
Simply put, it is naive to imagine that there is any hope that Libre-Halaal Software (or any form of non-proprietary software) can become basis for formulation of national policies in any Western society.
This is because of a number of a reasons, including:
- Intellectual Property Rights regime is an integral part of Western cultures. Even after it becomes obvious that the Western intellectual property rights regime is corrupt, economic interests will keep it in place. In many ways this parallels the history of Slavery in America.
- Western societies are primarily economically driven. Halaal and Haraam for anything, generally (if not always) remain fringe concepts.
- The Proprietary model is fully entrenched. And the course for using the proprietary model for internal and external exploitation is already fully charted.
In the West there is track record for where Libre-Halaal software and Internet services fit in Western societies. The advantages of being in harmony with nature has not been sufficient to bring GNU/Linux to the center – other than through economically driven bastardizations of Libre-Halaal software such as Appleization, Tivoization, Androidization, etc.
There is one aspect of halaal software and halaal Internet services that is congruent with Western cultures. It is of course “freedom” based.
6.4.1 Mostly Western Tear Point: Individual Privacy, Individual Liberty and Individual Autonomy
Some Westerners are now starting to see some problems with their current software and Internet services model. Autonomy, privacy and liberty are being crushed.
ByStar is the cure for those Westerners who value autonomy and liberty and who recognize the current ills and trends.
We offer the Libre-Halaal ByStar Digital Ecosystem and ByStar ideology to Americans the very same way that it is being offered to all societies – there to be understood and taken.
6.5 Libre-Halaal Software Based Formulation Of National Policies In Eastern Societies
Libre-Halaal software and Libre-Halaal Internet services have a much better chance of becoming a basis for formulation of national policies in Eastern societies.
This is because of a number of reasons including:
- Rejection of Western Intellectual Property Rights regime is easier and more beneficial to Eastern societies.
- Eastern societies are less economically driven and the general concept of halaal and haraam play a more significant role in Eastern societies.
- Proprietary software and Proprietary Internet services are used by the West as an instrument of exploitation and neo-colonialism against many Eastern societies in economic and political contexts. And whom ever objects to America and the american model is swiftly subjected to american freedom and american democracy through facebook and twiter.
- Unowned Halaal Software provides an alternative to the Proprietary American software. The collaborative model of Halaal Software permits for collective efforts for replacing American Proprietary Software.
We expand on these below.
6.5.1 Eastern Tear Point: Full Rejection Of Western IPR Regime
Any halaal software based formulation of national policies in eastern societies demands full rejection of the Western IPR regime.
It is much easier for Eastern societies to conclude that the Western IPR regime is morally wrong and that it is being used as an instrument of Western neo-colonialism.
Libre-Halaal ByStar Digital Ecosystem thrives when Western IPR is rejected.
The full beauty and power of ByStar will not be realized, until a culture whose ideology resonates with ByStar ideology, is ready to fully adopt ByStar.
6.5.2 Eastern Tear Point: Societal Autonomy
In the context of software, as an example, let’s consider the dependence of Arabs and Iranians on American proprietary software.
Today if you want to write in Persian or in Arabic, your main choice is Microsoft’s Proprietary-Haraam Windows environment. And in the business driven Western model, Perso-Arabic users are always second class citizens because they represent an insignificant market to the likes of American Microsoft and American Google. In other words computing and communication capabilities of Perso-Arabic societies is determined by Americans.
Eastern societies recognize this and see how Libre-Halaal Software can provide an alternative.
For example, what is maintained in http://www.persoarabic.org provides an alternative to the Proprietary Windows environment for Perso-Arabic processing. And provides societal autonomy with respect to software for Perso-Arabic cultures.
6.5.3 Worldly/Eastern Tear Point: Inherently Collaborative vs Inherently Competitive
The libre-halaal model creates an entirely new environment in terms of competition, collaboration, and value chain relationships. Libre-Halaal software and Internet Services are genuine public resources, not owned by anyone, freely available for reuse by anyone. They are created by society/humanity, for society/humanity.
This general proven collaborative model permits for collective efforts for replacing American Proprietary Software which from the perspective of an Eastern society is far more cost effective than the proprietary competitive model.
7 Our Responsibilities and Your Participation
The above picture is vast. Thus far, the entire By* formulation and development has been done by a very small team. Much of our work and much of our writing is in its early stages of evolution.
By* can only be significant if its usage is widespread and if By* collaborative development involves many. We have created many venues to facilitate collaboration. And now we ask you, to assist us in making the Libre-Halaal ByStar Digital Ecosystem widespread.
7.1 Assistance: Your analysis and critique
As a first step, we ask you to review what we have written and give us your critique. If you think our work has merit, we also ask you to help us in spreading the word. Please feel welcome to further distribute this document where appropriate.
You can send us your comments, criticisms and corrections through the following
URL:
http://www.by-star.net/contact
or by email through feedback@ our base domain which is
www.by-star.net.
7.2 Join us: an invitation to participate
The ByStar digital ecosystem initiative is big in scope and ambition. It is about an entirely new paradigm for Internet service deployment and usage. It isn’t about just another technology or service—it is a movement.
Something of this scope requires involvement and participation by multiple constituencies throughout society, including the engineering community, the business community, and the public at large. To enable such participation we have established a comprehensive framework for participation by all relevant constituencies. We invite you to join the Libre movement and participate in the role that suits you best. In particular we invite:
7.2.1 The engineering community:
To expand the Libre Services infrastructure, and to build more and better Libre Services.
The engineering and technology dimension of By* Halaal Digital Ecosystem is open and very collaborative.
7.2.2 The researchers and academic community:
To provide analysis and critique of the radical new Libre engineering and business models.
7.2.3 Public Policy Makers, Governments, Grant-making foundations
To provide sponsorship and funding for Libre Services development projects.
The entire By* design revolves around principles of planet wide Scalability, very distributed systems, autonomous control and end-to-end interactions. As such, By* has the potential for becoming a basis for national Internet services.
7.2.4 Philosophers, Ethicists, Sociologists:
To safeguard humanity.
As engineers, our focus has been manner-of-existence of software.
Consideration of what constitutes halaal software and halaal Internet services based on capabilities and usage is primarily the domain of ethicists.
7.2.5 Investors, Businessmen:
To deploy and deliver Libre-Halaal Digital Ecosystem in a commercial context. To finance commercial deployment of the Libre-Halaal ByStar Digital Ecosystem.
The open business plan itself describes further forms of participation, appropriate to the various intended audiences for the plan. A good starting point is: http://www.neda.com/strategicVision/businessPlan
Also, if appropriate please forward the following link to the corporate development department within your organization. http://www.neda.com/strategicVision
7.2.6 Reporters, The Media:
To publicize the concept, promote debate, and educate the public.
If you think what we are doing has merit, help us in spreading the word.
7.2.7 Content Producers:
Artists, filmmakers, writers, musicians and software developers who recognize by eliminating restrictions on the content that they produce, we are all better off.
ByStar offers much Libre-Halaal software to content producers who understand that the correct manner-of-existence of all content is Libre-Halaal.
7.2.8 The Public At Large:
To refuse Proprietary and to demand Libre.
To value their privacy and autonomy and to use the ByStar Federation of Autonomous Libre
Services.
8 Joining ByStar
| Joining |
A Strategy For Rapidly Becoming An Internet Application Service Provider |
||||||
| ByStar | Joining, Adopting and/or Licensing ByStar | ||||||
| As A Group | A Public Unsolicited Proposal | ||||||
Figure 12: Joining ByStar – En Masse and Individually
Successful Digital Ecosystems are dynamic. They grow and are ever evolving.
In the early stages of the evolution of ByStar we have adopted the strategy of limiting the size of our user base. A large active user base requires more support and is more difficult to maintain when service changes are frequent and when structural corrections may be needed.
At a certain point we would invite the public at large to use fully automated services to obtain ByStar accounts and start using ByStar. But, that is not now. ByStarEntityGenerator web services such as ByName.net ByAuthor.net ByWhere.net, etc. are in place. However, at this time we screen account requests individually.
8.1 Individually
Any individual wishing to join ByStar can make a request and we usually activate accounts for these requests. Please see http://www.by-star.net/joiningByStar for details.
8.2 En Masse
Groups of users (Autonomous ByStarEntities) such as student or staff at a university or High School or a church can join ByStar en masse and obtain ByName services.
Other ByStarEntity abstractions, for example, the deceased in a particular cemetery can join ByStar en masse and obtain ByMemory services.
In an article titled:
Joining, Adopting and/or Licensing ByStar
A Strategy For Rapidly Becoming An Internet Application Service Provider
A Proposal
http://www.by-star.net/PLPC/180040
We describe various options for those interested in joining, adopting and/or licensing ByStar.
References
- [1]
- " Mohsen BANAN ". " lsip design and implementation notes ". Permanent Libre Published Content "110501", Autonomously Self-Published, "December" 2007. http://www.neda.com/PLPC/110501.
- [2]
- " Mohsen BANAN ". " introducing convivial into globish ". Permanent Libre Published Content "120037", Autonomously Self-Published, "July" 2011. http://mohsen.banan.1.byname.net/PLPC/120037.
- [3]
- " Mohsen BANAN ". " the bystar applied model of federations of autonomous libre-halaal services ". Permanent Libre Published Content "180015", Autonomously Self-Published, "August" 2011. http://www.by-star.net/PLPC/180015.
- [4]
- " Mohsen BANAN ". " the for-profit and non-proprietary quadrant ". Permanent Libre Published Content "120042", Autonomously Self-Published, "July" 2011. mohsen.banan.1.byname.net/120042.
- [5]
- " Mohsen BANAN ". " sa-20000 home ". Permanent Libre Published Content "120044", Autonomously Self-Published, "September" 2012. http://mohsen.banan.1.byname.net/PLPC/120044.
- [6]
- " Mohsen BANAN ". "introducing halaal and haraam into globish based on moral philosophy of abstract halaal معرفیِ حلال و حرام به بقیهیِ دنیا ". Permanent Libre Published Content "120039", Autonomously Self-Published, "September" 2012. http://mohsen.1.banan.byname.net/120039.
- [7]
- " Mohsen BANAN ". " libre-halaal internet services defining halaal manner-of-existence of internet application services a non-proprietary model for delivery of internet services ". Permanent Libre Published Content "180045", Autonomously Self-Published, "September" 2013. http://www.by-star.net/PLPC/180045.
- [8]
- " Mohsen BANAN ". " libre-halaal software defining halaal manner-of-existence of software ". Permanent Libre Published Content "180044", Autonomously Self-Published, "August" 2013. http://www.by-star.net/PLPC/180044.
- [9]
- " Mohsen BANAN ". " the libre-halaal bystar digital ecosystem a unified and non-proprietary model for autonomous internet services a moral alterantive to the proprietary american digital ecosystem ". Permanent Libre Published Content "180016", Autonomously Self-Published, "September" 2013. http://www.by-star.net/PLPC/180016.
- [10]
- " Mohsen BANAN ". " the nature of poly-existentials: Basis for abolishment of the western intellectual property rights regime ". Permanent Libre Published Content "120033", Autonomously Self-Published, "September" 2013. http://mohsen.1.banan.byname.net/PLPC/120033.
- [11]
- Inc. " " Neda Communications. " blee and bxgnome: Bystar software-service continuum based convivial user environments ". Permanent Libre Published Content "180004", Autonomously Self-Published, "September" 2012. http://www.persoarabic.org/PLPC/180004.
- [12]
- Inc. " " Neda Communications. " a strategy for rapidly becoming an internet application service provider joining, adopting and/or licensing bystar a public unsolicited proposal ". Permanent Libre Published Content "180040", Autonomously Self-Published, "August" 2013. http://www.by-star.net/PLPC/180040.
- [13]
- Inc. " " Neda Communications. " bystar web facilities bystar content production, publication, and distribution services ". Permanent Libre Published Content "180038", Autonomously Self-Published, "May" 2013. http://www.by-star.net/PLPC/180038.
- [14]
- Inc. " " Neda Communications. " the libre-halaal bystar digital ecosystem an inversion to proprietary internet services model neda communication inc.’s open business plan ". Permanent Libre Published Content "180014", Autonomously Self-Published, "August" 2013. http://www.neda.com/strategicVision/businessPlan.
- [15]
- Mohsen BANAN Andrew Hammoude " " Neda Communications, Inc. " the by * family of libre services for network service providers: Generic proposal a strategy for rapid entry into the internet application services market a proposal ". Permanent Libre Published Content "110005", Autonomously Self-Published, "September" 2007. http://www.neda.com/PLPC/110005.